On the main screen type in:
*#06# for checking the IMEI (International Mobile Equipment Identity).
*#7780# reset to factory settings.
*#67705646# This will clear the LCD display(operator logo).
*#0000# To view software version.
*#2820# Bluetooth device address.
*#746025625# Sim clock allowed status.
#pw+1234567890+1# Shows if sim have restrictions.
*#92702689# – takes you to a secret menu where you may find some of the information below:
1. Displays Serial Number.
2. Displays the Month and Year of Manufacture
3. Displays (if there) the date where the phone was purchased (MMYY)
4. Displays the date of the last repair – if found (0000)
5. Shows life timer of phone (time passes since last start)
*#3370# – Enhanced Full Rate Codec (EFR) activation. Increase signal strength, better signal reception. It also help if u want to use GPRS and the service is not responding or too slow. Phone battery will drain faster though.
*#3370* – (EFR) deactivation. Phone will automatically restart. Increase battery life by 30% because phone receives less signal from network.
*#4720# – Half Rate Codec activation.
*#4720* – Half Rate Codec deactivation. The phone will automatically restart
If you forgot wallet code for Nokia S60 phone, use this code reset: *#7370925538#
Note, your data in the wallet will be erased. Phone will ask you the lock code. Default lock code is: 12345
Press *#3925538# to delete the contents and code of wallet.
Unlock service provider: Insert sim, turn phone on and press vol up(arrow keys) for 3 seconds, should say pin code. Press C,then press * message should flash, press * again and 04*pin*pin*pin# \
*#7328748263373738# resets security code.
Default security code is 12345
Change closed caller group (settings >security settings>user groups) to 00000 and ure phone will sound the message tone when you are near a radar speed trap. Setting it to 500 will cause your phone 2 set off security alarms at shop exits, gr8 for practical jokes! (works with some of the Nokia phones.) Press and hold “0″ on the main screen to open wap browser.
Saturday, May 23, 2009
Friday, May 22, 2009
Thursday, May 21, 2009
Windows Software
popup windows antivirus windows hide windows
microsoft windows alarm clock for windows cd-catalog for windows
child windows protect windows video for windows
install windows programming windows shutdown windows
lock windows fast windows shutdown net windows form control
saving privacy on windows xp alarm clock windows dos to windows
tweak windows xp proxy server for windows msn windows
commercial windows tweaking windows auto debug for windows
Other Searches
image software
Images: In Context! by Liquid Mirror Enterprises
A powerful, easy to use image editor that integrates directly into Windows. Images: In Context! is easily activated by simply right-clicking on the file or files you'd like to work with, allowing you to edit your digital photos with 70+ effects.
image utility context menu filter effect plugin crop rotate convert webpage redeye remover
title bar chane software
EPC Title Bar Changer by EpcSoft
EPC Title Bar Changer is intended to change the title bar and title icon of any windows,which can change text and icon of any window's title bar.
title bar chane title bar edit close all windows minimize all windows hide tray icon change texts icons windows add anti-boss key easily
registry fix software
! - Registry Fix by PIMASOFT
With Registry Fix 3.0 you can safely clean and repair Windows registry problems with a few simple mouse clicks! Problems with the Windows registry are a common cause of Windows crashes and error messages.
registry fix registry cleaner fix registry error fixer fix errors registry clean regclean cleaner fixer scan find fix pc errors fast optimization made easy
braun software
wAPI Monitor 2000 by Gregory Braun
wAPI Monitor 2000 is a small utility that allows you to monitor the debugger messages sent by many MS Windows applications and utilities. Facilities are also included to add diagnostic output messages to any software project that you are developing
braun wmonitor debug debugger monitor
screen recorder software
Huelix ScreenPlay Screen Recorder by Huelix Solutions
Huelix ScreenPlay Screen recorder records entire screen, a region of the screen or a specific window directly as compressed Windows Media Video. You can also record streaming video and record audio from a microphone or other source.
screen recorder screen video capture desktop recorder streaming video recorder
dns software
Simple DNS Plus by JH Software
The simple yet powerful DNS server for Windows 9x/NT/2000/XP/2003 With Simple DNS Plus you can hosts your own domain name, or simply speed up Internet access by running your own DNS server.
dns dhcp dns server windows dns server name server bind
java software
Excelsior JET for Windows by Excelsior, LLC
Excelsior JET is a Java Virtual Machine enhanced with Ahead-Of-Time (AOT) compilation. The AOT compiler transforms your classes and jars into high-performance Windows executables. Version for Linux on the Intel x86 platform is also available.
java exe dll compiler native ahead-of-time jvm
solitaire software
WORD² by John Heiting
WORD² is a shareware Windows solitaire word game in which you form and modify words at least four letters long using a deck of 53 cards. Points earned for each of up to thirteen words is determined by squaring the number of letters in the word.
solitaire word game card game word squared
viewer software
CodedColor PhotoStudio by 1STEIN Corporation
Merge the windows explorer with ACDSee, ThumbsPlus and Paintshop, and you get CodedColor, a powerful and easy to use photo-software to visualize / organize / edit / share / archive and print your digital photos with less than 4 MB download size!
viewer photo image editor graphics archive album publish jpg jpeg gif tif tiff bmp wmf organize print view thumbs catalog foto camera exif digital database batch conversion annotation iptc multimedia acdsee
screen-saver tool software
System ScreenSaver by Badevlad software company
http://www.filesland.com/software/windows-20.html
Run any OS command or application instead of the Windows screen-saver.
screen-saver tool system utility execute command replace screen-saver run os command application instead windows screen-saver
Page 21 out of 567 1...17 18 19 20 21 22 23 24 25 ...567
microsoft windows alarm clock for windows cd-catalog for windows
child windows protect windows video for windows
install windows programming windows shutdown windows
lock windows fast windows shutdown net windows form control
saving privacy on windows xp alarm clock windows dos to windows
tweak windows xp proxy server for windows msn windows
commercial windows tweaking windows auto debug for windows
Other Searches
image software
Images: In Context! by Liquid Mirror Enterprises
A powerful, easy to use image editor that integrates directly into Windows. Images: In Context! is easily activated by simply right-clicking on the file or files you'd like to work with, allowing you to edit your digital photos with 70+ effects.
image utility context menu filter effect plugin crop rotate convert webpage redeye remover
title bar chane software
EPC Title Bar Changer by EpcSoft
EPC Title Bar Changer is intended to change the title bar and title icon of any windows,which can change text and icon of any window's title bar.
title bar chane title bar edit close all windows minimize all windows hide tray icon change texts icons windows add anti-boss key easily
registry fix software
! - Registry Fix by PIMASOFT
With Registry Fix 3.0 you can safely clean and repair Windows registry problems with a few simple mouse clicks! Problems with the Windows registry are a common cause of Windows crashes and error messages.
registry fix registry cleaner fix registry error fixer fix errors registry clean regclean cleaner fixer scan find fix pc errors fast optimization made easy
braun software
wAPI Monitor 2000 by Gregory Braun
wAPI Monitor 2000 is a small utility that allows you to monitor the debugger messages sent by many MS Windows applications and utilities. Facilities are also included to add diagnostic output messages to any software project that you are developing
braun wmonitor debug debugger monitor
screen recorder software
Huelix ScreenPlay Screen Recorder by Huelix Solutions
Huelix ScreenPlay Screen recorder records entire screen, a region of the screen or a specific window directly as compressed Windows Media Video. You can also record streaming video and record audio from a microphone or other source.
screen recorder screen video capture desktop recorder streaming video recorder
dns software
Simple DNS Plus by JH Software
The simple yet powerful DNS server for Windows 9x/NT/2000/XP/2003 With Simple DNS Plus you can hosts your own domain name, or simply speed up Internet access by running your own DNS server.
dns dhcp dns server windows dns server name server bind
java software
Excelsior JET for Windows by Excelsior, LLC
Excelsior JET is a Java Virtual Machine enhanced with Ahead-Of-Time (AOT) compilation. The AOT compiler transforms your classes and jars into high-performance Windows executables. Version for Linux on the Intel x86 platform is also available.
java exe dll compiler native ahead-of-time jvm
solitaire software
WORD² by John Heiting
WORD² is a shareware Windows solitaire word game in which you form and modify words at least four letters long using a deck of 53 cards. Points earned for each of up to thirteen words is determined by squaring the number of letters in the word.
solitaire word game card game word squared
viewer software
CodedColor PhotoStudio by 1STEIN Corporation
Merge the windows explorer with ACDSee, ThumbsPlus and Paintshop, and you get CodedColor, a powerful and easy to use photo-software to visualize / organize / edit / share / archive and print your digital photos with less than 4 MB download size!
viewer photo image editor graphics archive album publish jpg jpeg gif tif tiff bmp wmf organize print view thumbs catalog foto camera exif digital database batch conversion annotation iptc multimedia acdsee
screen-saver tool software
System ScreenSaver by Badevlad software company
http://www.filesland.com/software/windows-20.html
Run any OS command or application instead of the Windows screen-saver.
screen-saver tool system utility execute command replace screen-saver run os command application instead windows screen-saver
Page 21 out of 567 1...17 18 19 20 21 22 23 24 25 ...567
Network & Internet::Trace & Ping Tools Category
NetScanTools Basic Edition 1.00
Basic free internet tools for the network engineer or anyone needing to test their network connection. We include basic Ping, Traceroute, Whois, Ping Scan, Graphical Ping and DNS tools in an integrated single solution program. These are simplified versions of the more extensive versions found in NetScanTools Pro. The software runs on Windows 7, Vista, 2008, 2003, XP and 2000 and includes full install/uninstall.
Read more -->
* License: Freeware
* Language: English
* Release: 2009-05-14
* Size: 2 Mb
* Cost: Free
Free Port Monitor 1.0
Free Port Monitor is one free network port monitoring software, it enables you to monitor all open TCP ports on the local and remote computer, show one alert message or send your one warning email once the your computer, web servers and network server becomes unavailable, it is one useful network tool from FreePortMonitor.com, at the best, it is one absolute freeware. This network tool is easy to use very much, and can work in silent background.
Read more -->
* License: Freeware
* Language: English
* Release: 2009-04-27
* Size: 643 Kb
* Cost: Free
PingInfoView 1.25
PingInfoView is a small utility that allows you to easily ping multiple host names and IP addresses, and watch the result in one table. It automatically ping to all hosts every number of seconds that you specify, and displays the number of succeed and failed pings, as well as the average ping time. You can also save the ping result into text/html/xml file, or copy it to the clipboard.
Read more -->
* License: Freeware
* Language: English
* Release: 2009-03-30
* Size: 40 Kb
* Cost: Free
NetInfo 6.8
NetInfo is a collection of 15 different state-of-the-art network diagnostic tools on a single, easy-to-use interface. Designed from first-hand experience, NetInfo allows businesses to more effectively combat network downtime by allowing network administrators, webmasters, and Internet service providers to more accurately isolate faults, simplify processing of diagnostic data and increase internal network security.
Read more -->
* License: Shareware
* Language: English
* Release: 2009-03-29
* Size: 1 Mb
* Cost: 39.99 $
Port Analyzer 1.0
Port Analyzer is a free network port analyzer software, it can capture and transmit all network data packets bypassing the protocol stack, provide packet capture and network analysis for the Windows platforms, developed by PortAnalyzer.com and released as one freeware, be free for everyone use, it is a handy network tool for normal users, programmers and network administrators. Program is easy to use very much, from beginners and specialists.
Read more -->
* License: Freeware
* Language: English
* Release: 2009-03-29
* Size: 682 Kb
* Cost: Free
Visual IP Trace 4.0e
Visual IP Trace helps identify hackers, validate websites, and investigate IP addresses. Trace analysis reports provide detailed information including the estimated physical location, network provider and worldwide whois information. The analysis reports enable users to verify a website prior to submitting confidential information, trace a hacker or suspect to their location, and report Internet abuse or illegal activity.
Read more -->
* License: Shareware
* Language: English
* Release: 2009-03-17
* Size: 3 Mb
* Cost: 39.95 $
PingPlotter Standard Edition 3.30.0s
PingPlotter Standard is a lightweight network monitoring and troubleshooting tool. It can run in the background collecting data while you continue to run applications, and then allow you to quickly look at the data in an intuitive graphical format when you experience problems (reduced call quality for VoIP, slowdowns or disconnects with applications, etc.). PingPlotter Standard is great at allowing you to collect data over time to see trends.
Read more -->
* License: Shareware
* Language: English
* Release: 2008-09-28
* Size: 2 Mb
* Cost: 24.95 $
PingCOPA Network Tools 3.01
PingCOPA Network Tools are an aid for network users when monitoring and diagnosing IP network problems. Speech output is provided to enable you to work on cables and hardware without looking at the computer monitor when testing IP network problems. Continuously monitor network computers, HTTP Web Servers, FTP Servers, POP3 Servers and SMTP Servers and be notified of problems by speech or email. Built in whois, nslookup and traceroute functions.
Read more -->
* License: Shareware
* Language: English
* Release: 2008-09-10
* Size: 6 Mb
* Cost: 24.95 $
WinSuperKit 6.3.1.573
WinSuperKit is a powerful network toolkit that is used to list ip address and MAC address of all PCs on network neighborhood, find ip address of a special host or host name of a specail ip address on internet or intranet, ping a host, trace routes and display the geographical location of the ip address. It can monitor network speed and compare files, can setup the date of your computer with network timer.
Read more -->
* License: Shareware
* Language: English
* Release: 2008-08-29
* Size: 13 Mb
* Cost: 79.00 $
Hardping Pro 1.1.1
Find all devices on your network even if they have a firewall. Hardping Pro pings devices at the hardware level which means it can't be blocked by personal firewalls. This makes it great as a ping utility on Windows networks and for MAC discovery. It is an ideal tool to use on large networks or any Wi-Fi networks to determine exactly which devices are connected to your network.
Read more -->
* License: Shareware
* Language: English
* Release: 2008-08-29
* Size: 536 Kb
* Cost: 24.95 $
FreeSysInfo 1.2
FreeSysInfo allows you to discover system and network information on your local machine or network computer. The tool used WMI ( Windows Management Instrumentation ) to discover full NDIS information, wireless network status and type, network adapters, system processes and services, serial communications and display information, hardware and connections status, user and system accounts, proxy settings, shared resource information and more.
Read more -->
* License: Freeware
* Language: English
* Release: 2008-06-22
* Size: 541 Kb
* Cost: Free
Colasoft MAC Scanner Pro 2.2
Colasoft MAC Scanner is a scan tool for scanning IP address and MAC address. It can automatically detect all subnets according to the IP addresses configured on multiple NICs of a machine and scan the MAC addresses and IP addresses of defined subnets as your need.
Read more -->
* License: Shareware
* Language: English
* Release: 2008-05-04
* Size: 5 Mb
* Cost: 199.00 $
WatchDog4.Biz Free Website Monitoring 1.0.3.0
WatchDog4.Biz is a free website availability monitoring and performance monitoring tool. It is a solution that helps you to get a true picture of availability and performance of your websites. Using WatchDog4.Biz you can always be aware whether your online business is down or up and estimate the efficiency of your web hosting. Uptime statistics reports, charts and diagrams built by the application provide detailed information on these points.
Read more -->
* License: Freeware
* Language: English, Russian
* Release: 2008-04-24
* Size: 5 Mb
* Cost: Free
Pingotron 4.2.0
Pingotron is made for network administrators, webmasters, and Internet service providers. Pingotron allows managing devices connected to a local network (computers, printers, etc.) and communication channels in TCP/IP networks. Basic features: 1) Custom ping time 2) Graphical and numeric representation of ping results 3) Generating lists by groups 4) Sound alarm, e-mail notifications, and blinking tray notification of failures.
Read more -->
* License: Shareware
* Language: English, Russian
* Release: 2008-04-19
* Size: 1 Mb
* Cost: 10.95 $
Active Whois Browser 3.1
Active Whois is an easy-to-use network tool for the retrieving of all information such as country, email and postal addresses for the owners of IP addresses and Internet domains. Unlike other WHOIS clients, Active Whois does not require special skills to collect the desired information. Its unique WHOIS-hyperlink feature allows you to browse a domain's databases as easily as you do the Web.
Read more -->
* License: Shareware
* Language: English
* Release: 2008-02-23
* Size: 1009 Kb
* Cost: 19.95 $
SI Trace 1.0
SI Trace is a free visual tool for Windows that traces the route of IP packets while they travel from your PC to the remote destination. The tool essentially allows you to see exactly where a connectivity problem is, no matter how far it is from your computer. The last host to respond to traceroute is the last host that is working properly. The first one that fails to respond is the faulty one.
Read more -->
* License: Freeware
* Language: English
* Release: 2007-07-15
* Size: 299 Kb
* Cost: Free
WebHopper Classic 1.1
WebHopper is a quick, easy-to-use Internet tool that lifts the lid on server routes, revealing the true location of Internet addresses and the circuitous routes by which we reach them. Its unique 'outside looking in' function holds up a mirror to your own computer to provide interesting and useful data about how your computer identifies itself on the Internet.
Read more -->
* License: Freeware
* Language: English
* Release: 2007-04-26
* Size: 830 Kb
* Cost: Free
EMCO Network Scanner 1.6.10
New and handy tool brought to you by EMCO Software; that enables network administrator to perform and schedule different scan operation on your network.
Read more -->
* License: Shareware
* Language: English
* Release: 2006-06-22
* Size: 3 Mb
* Cost: 235.00 $
Capturix NETWorks 3.10.154
Capturix NETWorks is a network utility software that ables you to test and diagnose all common problems from any network. It brings a group of very useful tools like: System Information that can show all information related with a specific network card or connection, Speed Meter, Route Information, IP config, Send Mail, Port Scanner with port description that have thousands of trojans port information and almost all protocols used for each port,
Read more -->
* License: Shareware
* Language: English, French, German, Italian, Portuguese
* Release: 2005-10-01
* Size: 3 Mb
* Cost: 19.99 $
http://www.vista-files.org/category/network-internet/trace-ping-tools/
eXpress IP Locator 1.2.3
Small freeware utility for offline retrieving the country information from IP-address or hostname, viewing IP-address blocks allocated for specified countries and seeking the country by code or code by country. Unlike from many other utilites, XIPL don't require the connection to internet.
Read more -->
* License: Freeware
* Language: English
* Release: 2004-10-04
* Size: 501 Kb
* Cost: Free
Basic free internet tools for the network engineer or anyone needing to test their network connection. We include basic Ping, Traceroute, Whois, Ping Scan, Graphical Ping and DNS tools in an integrated single solution program. These are simplified versions of the more extensive versions found in NetScanTools Pro. The software runs on Windows 7, Vista, 2008, 2003, XP and 2000 and includes full install/uninstall.
Read more -->
* License: Freeware
* Language: English
* Release: 2009-05-14
* Size: 2 Mb
* Cost: Free
Free Port Monitor 1.0
Free Port Monitor is one free network port monitoring software, it enables you to monitor all open TCP ports on the local and remote computer, show one alert message or send your one warning email once the your computer, web servers and network server becomes unavailable, it is one useful network tool from FreePortMonitor.com, at the best, it is one absolute freeware. This network tool is easy to use very much, and can work in silent background.
Read more -->
* License: Freeware
* Language: English
* Release: 2009-04-27
* Size: 643 Kb
* Cost: Free
PingInfoView 1.25
PingInfoView is a small utility that allows you to easily ping multiple host names and IP addresses, and watch the result in one table. It automatically ping to all hosts every number of seconds that you specify, and displays the number of succeed and failed pings, as well as the average ping time. You can also save the ping result into text/html/xml file, or copy it to the clipboard.
Read more -->
* License: Freeware
* Language: English
* Release: 2009-03-30
* Size: 40 Kb
* Cost: Free
NetInfo 6.8
NetInfo is a collection of 15 different state-of-the-art network diagnostic tools on a single, easy-to-use interface. Designed from first-hand experience, NetInfo allows businesses to more effectively combat network downtime by allowing network administrators, webmasters, and Internet service providers to more accurately isolate faults, simplify processing of diagnostic data and increase internal network security.
Read more -->
* License: Shareware
* Language: English
* Release: 2009-03-29
* Size: 1 Mb
* Cost: 39.99 $
Port Analyzer 1.0
Port Analyzer is a free network port analyzer software, it can capture and transmit all network data packets bypassing the protocol stack, provide packet capture and network analysis for the Windows platforms, developed by PortAnalyzer.com and released as one freeware, be free for everyone use, it is a handy network tool for normal users, programmers and network administrators. Program is easy to use very much, from beginners and specialists.
Read more -->
* License: Freeware
* Language: English
* Release: 2009-03-29
* Size: 682 Kb
* Cost: Free
Visual IP Trace 4.0e
Visual IP Trace helps identify hackers, validate websites, and investigate IP addresses. Trace analysis reports provide detailed information including the estimated physical location, network provider and worldwide whois information. The analysis reports enable users to verify a website prior to submitting confidential information, trace a hacker or suspect to their location, and report Internet abuse or illegal activity.
Read more -->
* License: Shareware
* Language: English
* Release: 2009-03-17
* Size: 3 Mb
* Cost: 39.95 $
PingPlotter Standard Edition 3.30.0s
PingPlotter Standard is a lightweight network monitoring and troubleshooting tool. It can run in the background collecting data while you continue to run applications, and then allow you to quickly look at the data in an intuitive graphical format when you experience problems (reduced call quality for VoIP, slowdowns or disconnects with applications, etc.). PingPlotter Standard is great at allowing you to collect data over time to see trends.
Read more -->
* License: Shareware
* Language: English
* Release: 2008-09-28
* Size: 2 Mb
* Cost: 24.95 $
PingCOPA Network Tools 3.01
PingCOPA Network Tools are an aid for network users when monitoring and diagnosing IP network problems. Speech output is provided to enable you to work on cables and hardware without looking at the computer monitor when testing IP network problems. Continuously monitor network computers, HTTP Web Servers, FTP Servers, POP3 Servers and SMTP Servers and be notified of problems by speech or email. Built in whois, nslookup and traceroute functions.
Read more -->
* License: Shareware
* Language: English
* Release: 2008-09-10
* Size: 6 Mb
* Cost: 24.95 $
WinSuperKit 6.3.1.573
WinSuperKit is a powerful network toolkit that is used to list ip address and MAC address of all PCs on network neighborhood, find ip address of a special host or host name of a specail ip address on internet or intranet, ping a host, trace routes and display the geographical location of the ip address. It can monitor network speed and compare files, can setup the date of your computer with network timer.
Read more -->
* License: Shareware
* Language: English
* Release: 2008-08-29
* Size: 13 Mb
* Cost: 79.00 $
Hardping Pro 1.1.1
Find all devices on your network even if they have a firewall. Hardping Pro pings devices at the hardware level which means it can't be blocked by personal firewalls. This makes it great as a ping utility on Windows networks and for MAC discovery. It is an ideal tool to use on large networks or any Wi-Fi networks to determine exactly which devices are connected to your network.
Read more -->
* License: Shareware
* Language: English
* Release: 2008-08-29
* Size: 536 Kb
* Cost: 24.95 $
FreeSysInfo 1.2
FreeSysInfo allows you to discover system and network information on your local machine or network computer. The tool used WMI ( Windows Management Instrumentation ) to discover full NDIS information, wireless network status and type, network adapters, system processes and services, serial communications and display information, hardware and connections status, user and system accounts, proxy settings, shared resource information and more.
Read more -->
* License: Freeware
* Language: English
* Release: 2008-06-22
* Size: 541 Kb
* Cost: Free
Colasoft MAC Scanner Pro 2.2
Colasoft MAC Scanner is a scan tool for scanning IP address and MAC address. It can automatically detect all subnets according to the IP addresses configured on multiple NICs of a machine and scan the MAC addresses and IP addresses of defined subnets as your need.
Read more -->
* License: Shareware
* Language: English
* Release: 2008-05-04
* Size: 5 Mb
* Cost: 199.00 $
WatchDog4.Biz Free Website Monitoring 1.0.3.0
WatchDog4.Biz is a free website availability monitoring and performance monitoring tool. It is a solution that helps you to get a true picture of availability and performance of your websites. Using WatchDog4.Biz you can always be aware whether your online business is down or up and estimate the efficiency of your web hosting. Uptime statistics reports, charts and diagrams built by the application provide detailed information on these points.
Read more -->
* License: Freeware
* Language: English, Russian
* Release: 2008-04-24
* Size: 5 Mb
* Cost: Free
Pingotron 4.2.0
Pingotron is made for network administrators, webmasters, and Internet service providers. Pingotron allows managing devices connected to a local network (computers, printers, etc.) and communication channels in TCP/IP networks. Basic features: 1) Custom ping time 2) Graphical and numeric representation of ping results 3) Generating lists by groups 4) Sound alarm, e-mail notifications, and blinking tray notification of failures.
Read more -->
* License: Shareware
* Language: English, Russian
* Release: 2008-04-19
* Size: 1 Mb
* Cost: 10.95 $
Active Whois Browser 3.1
Active Whois is an easy-to-use network tool for the retrieving of all information such as country, email and postal addresses for the owners of IP addresses and Internet domains. Unlike other WHOIS clients, Active Whois does not require special skills to collect the desired information. Its unique WHOIS-hyperlink feature allows you to browse a domain's databases as easily as you do the Web.
Read more -->
* License: Shareware
* Language: English
* Release: 2008-02-23
* Size: 1009 Kb
* Cost: 19.95 $
SI Trace 1.0
SI Trace is a free visual tool for Windows that traces the route of IP packets while they travel from your PC to the remote destination. The tool essentially allows you to see exactly where a connectivity problem is, no matter how far it is from your computer. The last host to respond to traceroute is the last host that is working properly. The first one that fails to respond is the faulty one.
Read more -->
* License: Freeware
* Language: English
* Release: 2007-07-15
* Size: 299 Kb
* Cost: Free
WebHopper Classic 1.1
WebHopper is a quick, easy-to-use Internet tool that lifts the lid on server routes, revealing the true location of Internet addresses and the circuitous routes by which we reach them. Its unique 'outside looking in' function holds up a mirror to your own computer to provide interesting and useful data about how your computer identifies itself on the Internet.
Read more -->
* License: Freeware
* Language: English
* Release: 2007-04-26
* Size: 830 Kb
* Cost: Free
EMCO Network Scanner 1.6.10
New and handy tool brought to you by EMCO Software; that enables network administrator to perform and schedule different scan operation on your network.
Read more -->
* License: Shareware
* Language: English
* Release: 2006-06-22
* Size: 3 Mb
* Cost: 235.00 $
Capturix NETWorks 3.10.154
Capturix NETWorks is a network utility software that ables you to test and diagnose all common problems from any network. It brings a group of very useful tools like: System Information that can show all information related with a specific network card or connection, Speed Meter, Route Information, IP config, Send Mail, Port Scanner with port description that have thousands of trojans port information and almost all protocols used for each port,
Read more -->
* License: Shareware
* Language: English, French, German, Italian, Portuguese
* Release: 2005-10-01
* Size: 3 Mb
* Cost: 19.99 $
http://www.vista-files.org/category/network-internet/trace-ping-tools/
eXpress IP Locator 1.2.3
Small freeware utility for offline retrieving the country information from IP-address or hostname, viewing IP-address blocks allocated for specified countries and seeking the country by code or code by country. Unlike from many other utilites, XIPL don't require the connection to internet.
Read more -->
* License: Freeware
* Language: English
* Release: 2004-10-04
* Size: 501 Kb
* Cost: Free
Download Trace Ip Address Software
Download Trace Ip Address Software
ip finder software
1st Net Scanner by Gonsoft
1st Net Scanner is a very useful IP Finder and Port Finder. It builds IP finder, port finder, IP scanner, port scanner and IP tracer, IP tracker, IP camera in one software. It can find IP address, search IP address, trace IP address and scan IP address. And it also can find port, search port and scan port. It''s easy and fast.
ip finder port finder ip scanner port scanner ip tracer ip tracker ip camera find ip address search ip address trace ip address scan ip address find port search port scan port
port scanner software
1st Ip Port Scanner by 1st Soft Inc
1st Ip Port Scanner is a very useful Ip Scanner and Port Scanner. It builds ip finder port finder ip scanner port scanner and ip tracer ip tracker ip camera in one software. It can find ip address,search ip address,trace ip address and scan ip address.And it also can find port,search port and scan port.It is easy and fast! 1st Ip Port Scanner allows for testing whether a remote computer is alive with three types ICMP, SYN and UDP.
port scanner port scan ip scan ip scanner ip finder find ip address ip trace ip address search ip relay ip search find ip ip camera ip tracker trace ip address ip tracer ip check ip address finder
ip finder software
1st Net Scanner by Gonsoft
1st Net Scanner is a very useful IP Finder and Port Finder. It builds IP finder, port finder, IP scanner, port scanner and IP tracer, IP tracker, IP camera in one software. It can find IP address, search IP address, trace IP address and scan IP address. And it also can find port, search port and scan port. It''s easy and fast.
ip finder port finder ip scanner port scanner ip tracer ip tracker ip camera find ip address search ip address trace ip address scan ip address find port search port scan port
port scanner software
1st Ip Port Scanner by 1st Soft Inc
1st Ip Port Scanner is a very useful Ip Scanner and Port Scanner. It builds ip finder port finder ip scanner port scanner and ip tracer ip tracker ip camera in one software. It can find ip address,search ip address,trace ip address and scan ip address.And it also can find port,search port and scan port.It is easy and fast! 1st Ip Port Scanner allows for testing whether a remote computer is alive with three types ICMP, SYN and UDP.
port scanner port scan ip scan ip scanner ip finder find ip address ip trace ip address search ip relay ip search find ip ip camera ip tracker trace ip address ip tracer ip check ip address finder
How to uninstall the Microsoft Java Virtual Machine (JVM)
Microsoft JVM is no longer supported by Microsoft, and it is recommended to remove it and install the Sun Microsystems JVM. The steps for removing Microsoft Java Virtual (JVM) are given below.
* Start -> Run
* Type RunDll32 advpack.dll,LaunchINFSection java.inf,UnInstall
* The un-install process begins. Click Yes to confirm.
* Reboot when prompted.
* After the machine restarts, delete the following items:
o the \%systemroot%\java folder
o the file java.pnf from the \%systemroot%\inf folder
o the two files jview.exe and wjview.exe from the \%systemroot%\system32 folder
o the HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Java VM registry subkey
o the HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\AdvancedOptions\JAVA_VM registry subkey (to remove the Microsoft Internet Explorer (IE) options)
* Microsoft Java is now removed.
You can download Sun's newer JVM for Windows at: http://java.sun.com/getjava/index.html
* Start -> Run
* Type RunDll32 advpack.dll,LaunchINFSection java.inf,UnInstall
* The un-install process begins. Click Yes to confirm.
* Reboot when prompted.
* After the machine restarts, delete the following items:
o the \%systemroot%\java folder
o the file java.pnf from the \%systemroot%\inf folder
o the two files jview.exe and wjview.exe from the \%systemroot%\system32 folder
o the HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Java VM registry subkey
o the HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\AdvancedOptions\JAVA_VM registry subkey (to remove the Microsoft Internet Explorer (IE) options)
* Microsoft Java is now removed.
You can download Sun's newer JVM for Windows at: http://java.sun.com/getjava/index.html
Windows Hacks, Tips and Tricks
I have some secret Windows tips and tricks here. Many are problems which you may encounter, but for which Windows does not provide a readymade solution.
Registry
Display a banner each time Windows boots
1. Start -> Run
2. Type regedit
3. Go to the key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WinLogon
4. Create a new string value in the right pane named LegalNoticeCaption and enter the value that you want to see in the menubar
5. Create a new string value and name it LegalNoticeText. Modify it and insert the message you want to display each time Windows boots.
Windows
Shutting down Windows the fastest way
1. Start -> Run
2. Type rundll.exe user.exe,exitwindows
Internet Explorer
Your browser logo shows something other than the IE logo. Maybe you have installed your ISP software and you have a different logo on the top right. How do you remove it?
1. Close all browser windows
2. Start -> Run
3. Type RunDLL32.EXE IEdkcs32.dll,Clear
4. Click on OK, and start Internet Explorer. You should find the old spinning IE logo.
Registry
Display a banner each time Windows boots
1. Start -> Run
2. Type regedit
3. Go to the key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WinLogon
4. Create a new string value in the right pane named LegalNoticeCaption and enter the value that you want to see in the menubar
5. Create a new string value and name it LegalNoticeText. Modify it and insert the message you want to display each time Windows boots.
Windows
Shutting down Windows the fastest way
1. Start -> Run
2. Type rundll.exe user.exe,exitwindows
Internet Explorer
Your browser logo shows something other than the IE logo. Maybe you have installed your ISP software and you have a different logo on the top right. How do you remove it?
1. Close all browser windows
2. Start -> Run
3. Type RunDLL32.EXE IEdkcs32.dll,Clear
4. Click on OK, and start Internet Explorer. You should find the old spinning IE logo.
How to change boot sequence between Windows and Linux
This is an outdated page. The future version will contain Grub.
Switching from Lilo to NTFS boot loader
Login as root and edit /etc/lilo.conf:
su
emacs /etc/lilo.conf
If you use any other editor, use it instead of emacs.
Insert the line
default=windows
First make sure you have the following lines in your lilo.conf
other = /dev/hda1
label = windows
After that, effect the changes by entering:
lilo
That should set Windows as the default boot loader and start Windows by default.
Switching from Lilo to NTFS boot loader
Login as root and edit /etc/lilo.conf:
su
emacs /etc/lilo.conf
If you use any other editor, use it instead of emacs.
Insert the line
default=windows
First make sure you have the following lines in your lilo.conf
other = /dev/hda1
label = windows
After that, effect the changes by entering:
lilo
That should set Windows as the default boot loader and start Windows by default.
Solaris Commands
Display RAM in Solaris
/usr/sbin/prtconf | grep Memory
Display hard disk space
df -k /home/
Display hard disk I/O statistics
/usr/bin/iostat -E
Show list of users
listusers
Display Solaris information
uname -X
Display Solaris OS version
uname -a
Show process IDs corresponding to sshd
You can either do this:
pgrep sshd
Or the old fashioned way:
ps -ef | grep sshd | awk '{print $2}'
/usr/sbin/prtconf | grep Memory
Display hard disk space
df -k /home/
Display hard disk I/O statistics
/usr/bin/iostat -E
Show list of users
listusers
Display Solaris information
uname -X
Display Solaris OS version
uname -a
Show process IDs corresponding to sshd
You can either do this:
pgrep sshd
Or the old fashioned way:
ps -ef | grep sshd | awk '{print $2}'
How to set up your own website with domain hosting
How to get domain hosting and set up your own web site
Do you want your own website like www.aruljohn.com.
Registering your domain name
If you only need to register your domain name like aruljohn.com, you need to register with a domain name registrars. Most charge a little more than $8 a year. It may take 24 to 48 hours for your own domain name to actually show up. Once it shows up, it probably shows up parked.
Web Hosting
Once you have your domain name on the Internet, you will need to find a decent web hosting company that will give you web space to host your files. There are many deals out there by companies such as Lunarpages, Dreamhost, etc. What you have to look for is the bandwidth, uptime per month, and web space, depending on the type of web site you have. For a site with very few images 5 GB bandwidth per month is enough. Those with graphics intensive pages like photographs will need to go for more.
I recommend Bluehost for hosting your website (or hosting+registering) if you are not sure where to host.
I would recommend you read several website reviews before making your decision.
Free Domain Registration with Web Hosting
Many web hosting companies also give free domain registration if you buy web space for a year or more. You will have to consider these kind of deals with caution. These companies may give you a hard time if you want to transfer your domain, usually at the end of the year.
You have finally bought your web space with a decent web hosting company. You will now need to point your DNS servers to point to the DNS servers given by new web space by entering their IP addresses in the control panel of the domain registrar. This will take a few minutes to a few hours to take effect. Once it is done, upload your files to your new web space via FTP or SFTP. You can use an FTP client like FileZilla to upload the files. The FTP server's IP address should be given in the email sent by the web hosting company. Your web site is up and
Do you want your own website like www.aruljohn.com.
Registering your domain name
If you only need to register your domain name like aruljohn.com, you need to register with a domain name registrars. Most charge a little more than $8 a year. It may take 24 to 48 hours for your own domain name to actually show up. Once it shows up, it probably shows up parked.
Web Hosting
Once you have your domain name on the Internet, you will need to find a decent web hosting company that will give you web space to host your files. There are many deals out there by companies such as Lunarpages, Dreamhost, etc. What you have to look for is the bandwidth, uptime per month, and web space, depending on the type of web site you have. For a site with very few images 5 GB bandwidth per month is enough. Those with graphics intensive pages like photographs will need to go for more.
I recommend Bluehost for hosting your website (or hosting+registering) if you are not sure where to host.
I would recommend you read several website reviews before making your decision.
Free Domain Registration with Web Hosting
Many web hosting companies also give free domain registration if you buy web space for a year or more. You will have to consider these kind of deals with caution. These companies may give you a hard time if you want to transfer your domain, usually at the end of the year.
You have finally bought your web space with a decent web hosting company. You will now need to point your DNS servers to point to the DNS servers given by new web space by entering their IP addresses in the control panel of the domain registrar. This will take a few minutes to a few hours to take effect. Once it is done, upload your files to your new web space via FTP or SFTP. You can use an FTP client like FileZilla to upload the files. The FTP server's IP address should be given in the email sent by the web hosting company. Your web site is up and
How to find the IP address of the sender in email - Gmail, Yahoo mail or Hotmail
When you receive an email, you receive more than just the message. The email comes with headers that carry important information that can tell where the email was sent from and possibly who sent it. For that, you would need to find the IP address of the sender. The tutorial below can help you find the IP address of the sender. Note that this will not work if the sender uses anonymous proxy servers.
First of all, the IP address is generally found in the headers enclosed beween square brackets, for instance, [129.130.1.1]
Finding IP address in Gmail
1. Log into your Gmail account with your username and password.
2. Open the mail.
3. To display the email headers,
* Click on the inverted triangle beside Reply. Select Show Orginal.
4. You may copy the headers and use my IP address detection script to ease the process. Or if you want to manually find the IP address, proceed to 5.
5. Look for Received: from followed by the IP address between square brackets [ ].( Received: from [69.138.30.1] by web31804.mail.mud.yahoo.com)
6 If you find more than one Received: from patterns, select the last one.
7 Track the IP address of the sender link http://aruljohn.com/track.pl
Finding IP address in Yahoo! Mail
1.Log into your Yahoo! mail with your username and password.
2.Click on Inbox or whichever folder you have stored your mail.
3.Open the mail.
4.If you do not see the headers above the mail message, your headers are not displayed. To display the headers,
◦Click on Options on the top-right corner
◦In the Mail Options page, click on General Preferences
◦Scroll down to Messages where you have the Headers option
◦Make sure that Show all headers on incoming messages is selected
◦Click on the Save button
◦Go back to the mails and open that mail
5.You should see similar headers like this:
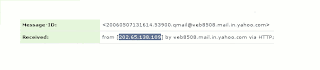
# You may copy the headers and use my IP address detection script to ease the process. Or if you want to manually find the IP address, proceed to 7.
# Look for Received: from followed by the IP address between square brackets [ ]. Here, it is 202.65.138.109.
That is be the IP address of the sender.
If there are many instances of Received: from with the IP address, select the IP address in the last pattern. If there are no instances of Received: from with the IP address, select the first IP address in X-Originating-IP.
# Track the IP address of the sender
Finding IP address in Hotmail
1. Log into your Hotmail account with your username and password.
2. Click on the Mail tab on the top.
3. Open the mail.
4. If you do not see the headers above the mail message, your headers are not displayed. To display the headers,
* Click on Options on the top-right corner
* In the Mail Options page, click on Mail Display Settings
* In Message Headers, make sure Advanced option is checked
* Click on Ok button
* Go back to the mails and open that mail
5. You should see the email headers now.
6. You may copy the headers and use my IP address detection script to ease the process. Or if you want to manually find the IP address, proceed to 7.
7. If you find a header with X-Originating-IP: followed by an IP address, that is the sender's IP address
Hotmail headers : Arul John In this case the IP address of the sender is [68.34.60.59]. Jump to step 9.
8. If you find a header with Received: from followed by a Gmail proxy like this
Hotmail headers : Arul John
Look for Received: from followed by IP address within square brackets[].
In this case, the IP address of the sender is [69.140.7.58]. Jump to step 9.
9. Or else if you have headers like this
Hotmail headers : Arul John
Look for Received: from followed by IP address within square brackets[].
In this case, the IP address of the sender is [61.83.145.129] (Spam mail). Jump to step 9.
10. * If you have multiple Received: from headers, eliminate the ones that have proxy.anyknownserver.com.
11. Track the IP address of the sender
IP Address Detection Script
I wrote a Perl script to automate this task for you. All you have to do is select your email service and copy your email headers in the box below.
You may do one of the following:
* You can copy all the headers from your email and paste them here.
In this case, the unnecessary headers (like Subject:) will be removed automatically.
* You can remove all headers except those beginning with
o X-Originating-IP:
o Received:
First of all, the IP address is generally found in the headers enclosed beween square brackets, for instance, [129.130.1.1]
Finding IP address in Gmail
1. Log into your Gmail account with your username and password.
2. Open the mail.
3. To display the email headers,
* Click on the inverted triangle beside Reply. Select Show Orginal.
4. You may copy the headers and use my IP address detection script to ease the process. Or if you want to manually find the IP address, proceed to 5.
5. Look for Received: from followed by the IP address between square brackets [ ].( Received: from [69.138.30.1] by web31804.mail.mud.yahoo.com)
6 If you find more than one Received: from patterns, select the last one.
7 Track the IP address of the sender link http://aruljohn.com/track.pl
Finding IP address in Yahoo! Mail
1.Log into your Yahoo! mail with your username and password.
2.Click on Inbox or whichever folder you have stored your mail.
3.Open the mail.
4.If you do not see the headers above the mail message, your headers are not displayed. To display the headers,
◦Click on Options on the top-right corner
◦In the Mail Options page, click on General Preferences
◦Scroll down to Messages where you have the Headers option
◦Make sure that Show all headers on incoming messages is selected
◦Click on the Save button
◦Go back to the mails and open that mail
5.You should see similar headers like this:

# You may copy the headers and use my IP address detection script to ease the process. Or if you want to manually find the IP address, proceed to 7.
# Look for Received: from followed by the IP address between square brackets [ ]. Here, it is 202.65.138.109.
That is be the IP address of the sender.
If there are many instances of Received: from with the IP address, select the IP address in the last pattern. If there are no instances of Received: from with the IP address, select the first IP address in X-Originating-IP.
# Track the IP address of the sender
Finding IP address in Hotmail
1. Log into your Hotmail account with your username and password.
2. Click on the Mail tab on the top.
3. Open the mail.
4. If you do not see the headers above the mail message, your headers are not displayed. To display the headers,
* Click on Options on the top-right corner
* In the Mail Options page, click on Mail Display Settings
* In Message Headers, make sure Advanced option is checked
* Click on Ok button
* Go back to the mails and open that mail
5. You should see the email headers now.
6. You may copy the headers and use my IP address detection script to ease the process. Or if you want to manually find the IP address, proceed to 7.
7. If you find a header with X-Originating-IP: followed by an IP address, that is the sender's IP address
Hotmail headers : Arul John In this case the IP address of the sender is [68.34.60.59]. Jump to step 9.
8. If you find a header with Received: from followed by a Gmail proxy like this
Hotmail headers : Arul John
Look for Received: from followed by IP address within square brackets[].
In this case, the IP address of the sender is [69.140.7.58]. Jump to step 9.
9. Or else if you have headers like this
Hotmail headers : Arul John
Look for Received: from followed by IP address within square brackets[].
In this case, the IP address of the sender is [61.83.145.129] (Spam mail). Jump to step 9.
10. * If you have multiple Received: from headers, eliminate the ones that have proxy.anyknownserver.com.
11. Track the IP address of the sender
IP Address Detection Script
I wrote a Perl script to automate this task for you. All you have to do is select your email service and copy your email headers in the box below.
You may do one of the following:
* You can copy all the headers from your email and paste them here.
In this case, the unnecessary headers (like Subject:) will be removed automatically.
* You can remove all headers except those beginning with
o X-Originating-IP:
o Received:
Hacking Tools Warez Rapidshare Download
Please avoid searching for terms such as: Hacking Tools warez, Hacking Tools crack, Hacking Tools serial, Hacking Tools full - as this may give false results or no results
Results for Hacking ToolsSizeDownloads
Download Hacking Tools Medium614 Times
Hacking Tools Full Version Medium240 Times
Hacking Tools (May 2009) Medium919 Times
Fbi Hacking Tools 11 You Ll Be Surprised [Pirate Access Direct] 7 MB37 Times
Windows Hacking Tools [Pirate Access Direct] 4 MB28 Times
Top 10 Vital Hacking Software And Tools 24 MB28 Times
App > Top 10 Vital Hacking Software And Tools 24 MB18 Times
Orkut Hacking Scripts and Tools
link working but not working wht u think u jus t serch whts right link
http://modeo.com/episodes/23256009-Orkut-Hacking-Scripts-and-Tools
Windows Hacking Tools Full Download
http://www.pirateaccess.com/download-windows-hacking-tools-12382607416452.html
Results for Hacking ToolsSizeDownloads
Download Hacking Tools Medium614 Times
Hacking Tools Full Version Medium240 Times
Hacking Tools (May 2009) Medium919 Times
Fbi Hacking Tools 11 You Ll Be Surprised [Pirate Access Direct] 7 MB37 Times
Windows Hacking Tools [Pirate Access Direct] 4 MB28 Times
Top 10 Vital Hacking Software And Tools 24 MB28 Times
App > Top 10 Vital Hacking Software And Tools 24 MB18 Times
Orkut Hacking Scripts and Tools
link working but not working wht u think u jus t serch whts right link
http://modeo.com/episodes/23256009-Orkut-Hacking-Scripts-and-Tools
Windows Hacking Tools Full Download
http://www.pirateaccess.com/download-windows-hacking-tools-12382607416452.html
how to hack Bluetooth Devices
Must have Bluetooth hacking tools
In English, Security, Techiebluetooth, hacker tools, hacking tools
hide
Google Search Results
You arrived here after searching for the following phrases:
* hacking
* tools
Click a phrase to jump to the first occurrence, or return to the search results.
This is a lis of the essential Bleutooth hacking tools, mostly for the Linux
platform, that can be used to search out and hack Bluetooth-enabled
devices.
Discovering Bluetooth Devices
BlueScanner - BlueScanner searches out for
Bluetooth-enabled devices. It will try to extract as much information
as possible for each newly discovered device. Download BlueScan.
BlueSniff - BlueSniff is a GUI-based utility for finding discoverable and hidden Bluetooth-enabled devices. Download BlueSniff.
BTBrowser - Bluetooth Browser is a J2ME application that
can browse and explore the technical specification of surrounding
Bluetooth-enabled devices. You can browse device information and all
supported profiles and service records of each device. BTBrowser works
on phones that supports JSR-82 - the Java Bluetooth specification. Download BTBrowser.
BTCrawler -BTCrawler is a scanner for Windows
Mobile based devices. It scans for other devices in range and performs
service query. It implements the BlueJacking and BlueSnarfing attacks. Download BTCrawler.
Hacking Bluetooth Devices
BlueBugger -BlueBugger exploits the BlueBug vulnerability.
BlueBug is the name of a set of Bluetooth security holes found in some
Bluetooth-enabled mobile phones. By exploiting those vulnerabilities,
one can gain an unauthorized access to the phone-book, calls lists and
other private information. Download BlueBugger.
CIHWB - Can I Hack With Bluetooth (CIHWB) is a Bluetooth
security auditing framework for Windows Mobile 2005. Currently it only
support some Bluetooth exploits and tools like BlueSnarf, BlueJack, and
some DoS attacks. Should work on any PocketPC with the Microsoft
Bluetooth stack. Download CIHWB.
Bluediving - Bluediving is a Bluetooth penetration testing
suite. It implements attacks like Bluebug, BlueSnarf, BlueSnarf++,
BlueSmack, has features such as Bluetooth address spoofing, an AT and a
RFCOMM socket shell and implements tools like carwhisperer, bss, L2CAP
packetgenerator, L2CAP connection resetter, RFCOMM scanner and
greenplaque scanning mode. Download Bluediving.
Transient Bluetooth Environment Auditor - T-BEAR is a
security-auditing platform for Bluetooth-enabled devices. The platform
consists of Bluetooth discovery tools, sniffing tools and various
cracking tools. Download T-BEAR.
Bluesnarfer - Bluesnarfer will download the phone-book of any mobile device vulnerable to Bluesnarfing.
Bluesnarfing is a serious security flow discovered in several
Bluetooth-enabled mobile phones. If a mobile phone is vulnerable, it is
possible to connect to the phone without alerting the owner, and gain
access to restricted portions of the stored data. Download Bluesnarfer.
BTcrack - BTCrack is a Bluetooth Pass phrase (PIN) cracking
tool. BTCrack aims to reconstruct the Passkey and the Link key from
captured Pairing exchanges. Download BTcrack.
Blooover II - Blooover II is a J2ME-based auditing tool. It
is intended to serve as an auditing tool to check whether a mobile
phone is vulnerable. Download Blooover II.
BlueTest - BlueTest is a Perl script designed to do data extraction from vulnerable Bluetooth-enabled devices. Download BlueTest.
BTAudit - BTAudit is a set of programs and scripts for auditing Bluetooth-enabled devices. Download BTAuding.
* Penetration Testing Tools
* Great list of hacking tools
* splmap 0.6 released
* VoIP Hacking software
* Free SQL Injection Scanners
software
http://sourceforge.net/project/platformdownload.php?group_id=195755
http://bluesniff.shmoo.com/bluesniff-0.1.tar.gz
http://www.benhui.net/bluetooth/btbrowser.html
http://www.silentservices.de/btCrawler.html
http://www.remote-exploit.org/codes/bluebugger/bluebugger-0.1.tar.gz
http://sourceforge.net/project/showfiles.php?group_id=173145
http://freshmeat.net/redir/t-bear/67412/url_tgz/tbear.tar.gz
http://www.salzburgresearch.at/research/publications_detail_e.php?pub_id=152http://www.alighieri.org/tools/bluesnarfer.tar.gz
http://trifinite.org/Downloads/Blooover2.jar
http://packetstorm.linuxsecurity.com/wireless/bluetest.pl.txt
http://www.betaversion.net/btdsd/download/bt_audit-0.1.1.tar.gz
In English, Security, Techiebluetooth, hacker tools, hacking tools
hide
Google Search Results
You arrived here after searching for the following phrases:
* hacking
* tools
Click a phrase to jump to the first occurrence, or return to the search results.
This is a lis of the essential Bleutooth hacking tools, mostly for the Linux
platform, that can be used to search out and hack Bluetooth-enabled
devices.
Discovering Bluetooth Devices
BlueScanner - BlueScanner searches out for
Bluetooth-enabled devices. It will try to extract as much information
as possible for each newly discovered device. Download BlueScan.
BlueSniff - BlueSniff is a GUI-based utility for finding discoverable and hidden Bluetooth-enabled devices. Download BlueSniff.
BTBrowser - Bluetooth Browser is a J2ME application that
can browse and explore the technical specification of surrounding
Bluetooth-enabled devices. You can browse device information and all
supported profiles and service records of each device. BTBrowser works
on phones that supports JSR-82 - the Java Bluetooth specification. Download BTBrowser.
BTCrawler -BTCrawler is a scanner for Windows
Mobile based devices. It scans for other devices in range and performs
service query. It implements the BlueJacking and BlueSnarfing attacks. Download BTCrawler.
Hacking Bluetooth Devices
BlueBugger -BlueBugger exploits the BlueBug vulnerability.
BlueBug is the name of a set of Bluetooth security holes found in some
Bluetooth-enabled mobile phones. By exploiting those vulnerabilities,
one can gain an unauthorized access to the phone-book, calls lists and
other private information. Download BlueBugger.
CIHWB - Can I Hack With Bluetooth (CIHWB) is a Bluetooth
security auditing framework for Windows Mobile 2005. Currently it only
support some Bluetooth exploits and tools like BlueSnarf, BlueJack, and
some DoS attacks. Should work on any PocketPC with the Microsoft
Bluetooth stack. Download CIHWB.
Bluediving - Bluediving is a Bluetooth penetration testing
suite. It implements attacks like Bluebug, BlueSnarf, BlueSnarf++,
BlueSmack, has features such as Bluetooth address spoofing, an AT and a
RFCOMM socket shell and implements tools like carwhisperer, bss, L2CAP
packetgenerator, L2CAP connection resetter, RFCOMM scanner and
greenplaque scanning mode. Download Bluediving.
Transient Bluetooth Environment Auditor - T-BEAR is a
security-auditing platform for Bluetooth-enabled devices. The platform
consists of Bluetooth discovery tools, sniffing tools and various
cracking tools. Download T-BEAR.
Bluesnarfer - Bluesnarfer will download the phone-book of any mobile device vulnerable to Bluesnarfing.
Bluesnarfing is a serious security flow discovered in several
Bluetooth-enabled mobile phones. If a mobile phone is vulnerable, it is
possible to connect to the phone without alerting the owner, and gain
access to restricted portions of the stored data. Download Bluesnarfer.
BTcrack - BTCrack is a Bluetooth Pass phrase (PIN) cracking
tool. BTCrack aims to reconstruct the Passkey and the Link key from
captured Pairing exchanges. Download BTcrack.
Blooover II - Blooover II is a J2ME-based auditing tool. It
is intended to serve as an auditing tool to check whether a mobile
phone is vulnerable. Download Blooover II.
BlueTest - BlueTest is a Perl script designed to do data extraction from vulnerable Bluetooth-enabled devices. Download BlueTest.
BTAudit - BTAudit is a set of programs and scripts for auditing Bluetooth-enabled devices. Download BTAuding.
* Penetration Testing Tools
* Great list of hacking tools
* splmap 0.6 released
* VoIP Hacking software
* Free SQL Injection Scanners
software
http://sourceforge.net/project/platformdownload.php?group_id=195755
http://bluesniff.shmoo.com/bluesniff-0.1.tar.gz
http://www.benhui.net/bluetooth/btbrowser.html
http://www.silentservices.de/btCrawler.html
http://www.remote-exploit.org/codes/bluebugger/bluebugger-0.1.tar.gz
http://sourceforge.net/project/showfiles.php?group_id=173145
http://freshmeat.net/redir/t-bear/67412/url_tgz/tbear.tar.gz
http://www.salzburgresearch.at/research/publications_detail_e.php?pub_id=152http://www.alighieri.org/tools/bluesnarfer.tar.gz
http://trifinite.org/Downloads/Blooover2.jar
http://packetstorm.linuxsecurity.com/wireless/bluetest.pl.txt
http://www.betaversion.net/btdsd/download/bt_audit-0.1.1.tar.gz
Places that viruses and Trojans hide on start up
1. START-UP FOLDER. Windows opens every item in the Start Menu's Start Up folder. This folder is prominent in the Programs folder of the Start Menu.
Notice that I did not say that Windows "runs" every program that is represented in the Start Up folder. I said it "opens every item." There's an important difference.
Programs represented in the Start Up folder will run, of course. But you can have shortcuts in the Start Up folder that represent documents, not programs.
For example, if you put a Microsoft Word document in the Start Up folder, Word will run and automatically open that document at bootup; if you put a WAV file there, your audio software will play the music at bootup, and if you put a Web-page Favourites there, Internet Explorer (or your own choice of a browser) will run and open that Web page for you when the computer starts up. (The examples cited here could just as easily be shortcuts to a WAV file or a Word document, and so on.)
2. REGISTRY. Windows executes all instructions in the "Run" section of the Windows Registry. Items in the "Run" section (and in other parts of the Registry listed below) can be programs or files that programs open (documents), as explained in No. 1 above.
3. REGISTRY. Windows executes all instructions in the "RunServices" section of the Registry.
4. REGISTRY. Windows executes all instructions in the "RunOnce" part of the Registry.
5. REGISTRY. Windows executes instructions in the "RunServicesOnce" section of the Registry. (Windows uses the two "RunOnce" sections to run programs a single time only, usually on the next bootup after a program installation.)
7. REGISTRY. Windows executes instructions in the HKEY_CLASSES_ROOT\exefile\shell\open\command "%1" %* section of the Registry. Any command imbedded here will open when any exe file is executed.
Other possibles:
[HKEY_CLASSES_ROOT\exefile\shell\open\command] ="\"%1\" %*"
[HKEY_CLASSES_ROOT\comfile\shell\open\command] ="\"%1\" %*"
[HKEY_CLASSES_ROOT\batfile\shell\open\command] ="\"%1\" %*"
[HKEY_CLASSES_ROOT\htafile\Shell\Open\Command] ="\"%1\" %*"
[HKEY_CLASSES_ROOT\piffile\shell\open\command] ="\"%1\" %*"
[HKEY_LOCAL_MACHINE\Software\CLASSES\batfile\shell\open\command] ="\"%1\"
%*"
[HKEY_LOCAL_MACHINE\Software\CLASSES\comfile\shell\open\command] ="\"%1\"
%*"
[HKEY_LOCAL_MACHINE\Software\CLASSES\exefile\shell\open\command] ="\"%1\"
%*"
[HKEY_LOCAL_MACHINE\Software\CLASSES\htafile\Shell\Open\Command] ="\"%1\"
%*"
[HKEY_LOCAL_MACHINE\Software\CLASSES\piffile\shell\open\command] ="\"%1\"
%*"
If keys don't have the "\"%1\" %*" value as shown, and are changed to something like "\"somefilename.exe %1\" %*" than they are automatically invoking the specified file.
8. BATCH FILE. Windows executes all instructions in the Winstart batch file, located in the Windows folder. (This file is unknown to nearly all Windows users and most Windows experts, and might not exist on your system. You can easily create it, however. Note that some versions of Windows call the Windows folder the "WinNT" folder.) The full filename is WINSTART.BAT.
9. INITIALIZATION FILE. Windows executes instructions in the "RUN=" line in the WIN.INI file, located in the Windows (or WinNT) folder.
10. INITIALIZATION FILE. Windows executes instructions in the "LOAD=" line in the WIN.INI file, located in the Windows (or WinNT) folder.
It also runs things in shell= in System.ini or c:\windows\system.ini:
[boot]
shell=explorer.exe C:\windows\filename
The file name following explorer.exe will start whenever Windows starts.
As with Win.ini, file names might be preceeded by considerable space on such a line, to reduce the chance that they will be seen. Normally, the full path of the file will be included in this entry. If not, check the \Windows directory
11. RELAUNCHING. Windows reruns programs that were running when Windows shut down. Windows cannot do this with most non-Microsoft programs, but it will do it easily with Internet Explorer and with Windows Explorer, the file-and-folder manager built into Windows. If you have Internet Explorer open when you shut Windows down, Windows will reopen IE with the same page open when you boot up again. (If this does not happen on your Windows PC, someone has turned that feature off. Use Tweak UI, the free Microsoft Windows user interface manager, to reactivate "Remember Explorer settings," or whatever it is called in your version of Windows.)
12. TASK SCHEDULER. Windows executes autorun instructions in the Windows Task Scheduler (or any other scheduler that supplements or replaces the Task Scheduler). The Task Scheduler is an official part of all Windows versions except the first version of Windows 95, but is included in Windows 95 if the Microsoft Plus Pack was installed.
13. SECONDARY INSTRUCTIONS. Programs that Windows launches at startup are free to launch separate programs on their own. Technically, these are not programs that Windows launches, but they are often indistinguishable from ordinary auto-running programs if they are launched right after their "parent" programs run.
14. C:\EXPLORER.EXE METHOD.
C:\Explorer.exe
Windows loads explorer.exe (typically located in the Windows directory)during the boot process. However, if c:\explorer.exe exists, it will be executed instead of the Windows explorer.exe. If c:\explorer.exe is corrupt, the user will effectively be locked out of their system after they reboot.
If c:\explorer.exe is a trojan, it will be executed. Unlike all other autostart methods, there is no need for any file or registry changes - the file just simply has to be named c:\explorer.exe
15. ADDITIONAL METHODS.
Additional autostart methods. The first two are used by Trojan SubSeven 2.2.
HKEY_LOCAL_MACHINE\Software\Microsoft\Active Setup\Installed Components
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\Currentversion\explorer\Usershell folders
Icq Inet
[HKEY_CURRENT_USER\Software\Mirabilis\ICQ\Agent\Apps\test]
"Path"="test.exe"
"Startup"="c:\\test"
"Parameters"=""
"Enable"="Yes"
[HKEY_CURRENT_USER\Software\Mirabilis\ICQ\Agent\Apps\]
This key specifies that all applications will be executed if ICQNET Detects an Internet Connection.
[HKEY_LOCAL_MACHINE\Software\CLASSES\ShellScrap] ="Scrap object"
"NeverShowExt"=""
This key changes your file's specified extension.
Notice that I did not say that Windows "runs" every program that is represented in the Start Up folder. I said it "opens every item." There's an important difference.
Programs represented in the Start Up folder will run, of course. But you can have shortcuts in the Start Up folder that represent documents, not programs.
For example, if you put a Microsoft Word document in the Start Up folder, Word will run and automatically open that document at bootup; if you put a WAV file there, your audio software will play the music at bootup, and if you put a Web-page Favourites there, Internet Explorer (or your own choice of a browser) will run and open that Web page for you when the computer starts up. (The examples cited here could just as easily be shortcuts to a WAV file or a Word document, and so on.)
2. REGISTRY. Windows executes all instructions in the "Run" section of the Windows Registry. Items in the "Run" section (and in other parts of the Registry listed below) can be programs or files that programs open (documents), as explained in No. 1 above.
3. REGISTRY. Windows executes all instructions in the "RunServices" section of the Registry.
4. REGISTRY. Windows executes all instructions in the "RunOnce" part of the Registry.
5. REGISTRY. Windows executes instructions in the "RunServicesOnce" section of the Registry. (Windows uses the two "RunOnce" sections to run programs a single time only, usually on the next bootup after a program installation.)
7. REGISTRY. Windows executes instructions in the HKEY_CLASSES_ROOT\exefile\shell\open\command "%1" %* section of the Registry. Any command imbedded here will open when any exe file is executed.
Other possibles:
[HKEY_CLASSES_ROOT\exefile\shell\open\command] ="\"%1\" %*"
[HKEY_CLASSES_ROOT\comfile\shell\open\command] ="\"%1\" %*"
[HKEY_CLASSES_ROOT\batfile\shell\open\command] ="\"%1\" %*"
[HKEY_CLASSES_ROOT\htafile\Shell\Open\Command] ="\"%1\" %*"
[HKEY_CLASSES_ROOT\piffile\shell\open\command] ="\"%1\" %*"
[HKEY_LOCAL_MACHINE\Software\CLASSES\batfile\shell\open\command] ="\"%1\"
%*"
[HKEY_LOCAL_MACHINE\Software\CLASSES\comfile\shell\open\command] ="\"%1\"
%*"
[HKEY_LOCAL_MACHINE\Software\CLASSES\exefile\shell\open\command] ="\"%1\"
%*"
[HKEY_LOCAL_MACHINE\Software\CLASSES\htafile\Shell\Open\Command] ="\"%1\"
%*"
[HKEY_LOCAL_MACHINE\Software\CLASSES\piffile\shell\open\command] ="\"%1\"
%*"
If keys don't have the "\"%1\" %*" value as shown, and are changed to something like "\"somefilename.exe %1\" %*" than they are automatically invoking the specified file.
8. BATCH FILE. Windows executes all instructions in the Winstart batch file, located in the Windows folder. (This file is unknown to nearly all Windows users and most Windows experts, and might not exist on your system. You can easily create it, however. Note that some versions of Windows call the Windows folder the "WinNT" folder.) The full filename is WINSTART.BAT.
9. INITIALIZATION FILE. Windows executes instructions in the "RUN=" line in the WIN.INI file, located in the Windows (or WinNT) folder.
10. INITIALIZATION FILE. Windows executes instructions in the "LOAD=" line in the WIN.INI file, located in the Windows (or WinNT) folder.
It also runs things in shell= in System.ini or c:\windows\system.ini:
[boot]
shell=explorer.exe C:\windows\filename
The file name following explorer.exe will start whenever Windows starts.
As with Win.ini, file names might be preceeded by considerable space on such a line, to reduce the chance that they will be seen. Normally, the full path of the file will be included in this entry. If not, check the \Windows directory
11. RELAUNCHING. Windows reruns programs that were running when Windows shut down. Windows cannot do this with most non-Microsoft programs, but it will do it easily with Internet Explorer and with Windows Explorer, the file-and-folder manager built into Windows. If you have Internet Explorer open when you shut Windows down, Windows will reopen IE with the same page open when you boot up again. (If this does not happen on your Windows PC, someone has turned that feature off. Use Tweak UI, the free Microsoft Windows user interface manager, to reactivate "Remember Explorer settings," or whatever it is called in your version of Windows.)
12. TASK SCHEDULER. Windows executes autorun instructions in the Windows Task Scheduler (or any other scheduler that supplements or replaces the Task Scheduler). The Task Scheduler is an official part of all Windows versions except the first version of Windows 95, but is included in Windows 95 if the Microsoft Plus Pack was installed.
13. SECONDARY INSTRUCTIONS. Programs that Windows launches at startup are free to launch separate programs on their own. Technically, these are not programs that Windows launches, but they are often indistinguishable from ordinary auto-running programs if they are launched right after their "parent" programs run.
14. C:\EXPLORER.EXE METHOD.
C:\Explorer.exe
Windows loads explorer.exe (typically located in the Windows directory)during the boot process. However, if c:\explorer.exe exists, it will be executed instead of the Windows explorer.exe. If c:\explorer.exe is corrupt, the user will effectively be locked out of their system after they reboot.
If c:\explorer.exe is a trojan, it will be executed. Unlike all other autostart methods, there is no need for any file or registry changes - the file just simply has to be named c:\explorer.exe
15. ADDITIONAL METHODS.
Additional autostart methods. The first two are used by Trojan SubSeven 2.2.
HKEY_LOCAL_MACHINE\Software\Microsoft\Active Setup\Installed Components
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\Currentversion\explorer\Usershell folders
Icq Inet
[HKEY_CURRENT_USER\Software\Mirabilis\ICQ\Agent\Apps\test]
"Path"="test.exe"
"Startup"="c:\\test"
"Parameters"=""
"Enable"="Yes"
[HKEY_CURRENT_USER\Software\Mirabilis\ICQ\Agent\Apps\]
This key specifies that all applications will be executed if ICQNET Detects an Internet Connection.
[HKEY_LOCAL_MACHINE\Software\CLASSES\ShellScrap] ="Scrap object"
"NeverShowExt"=""
This key changes your file's specified extension.
Remote Spying Software
Track Their Email, IMs & Passwords
Remote Spy Software Affil.
http://www.securetactics.com/spyvector
Remote Spy Software Affil.
http://www.securetactics.com/spyvector
email id hacking
hacking tools software
but right link iam not sure i am just changing link
becu iam not hacker
http://akashkpal.com/
but right link iam not sure i am just changing link
becu iam not hacker
http://akashkpal.com/
Wednesday, May 20, 2009
Cloud Antivirus Beta
Cloud Antivirus is designed by Panda Security. The application is well known over more than 100 hundred countries, you don?t need to worry when you are using Cloud Antivirus. The application consists of an anti-virus and also accompanied by an anti-spyware. You just need to install the software on your system and it will work quietly in your task bar.
Advantage
It is compatible on both XP and Vista Platforms.
It also works when you are connected.
Disadvantage
The application is available in English version only.
CloudAntivirus.exe click on server 1 or 2
Advantage
It is compatible on both XP and Vista Platforms.
It also works when you are connected.
Disadvantage
The application is available in English version only.
CloudAntivirus.exe click on server 1 or 2
HOW TO HACK Bank Account Tracking 5.3
BUT ITS NOT FREE OK.
http://en.kioskea.net/telecharger/telecharger-1234-bank-account-tracking ITS SITE LINK BUT IAM NOT SURE
JUST MAIL ME b_akash@rocketmail.com
http://en.kioskea.net/telecharger/telecharger-1234-bank-account-tracking ITS SITE LINK BUT IAM NOT SURE
JUST MAIL ME b_akash@rocketmail.com
how to hack email id
iam tell u how to hack id but now its not free for every one
you just email me what's your suggestion but not free ok..
how to hack password of different users in yahoo,google and other stuff.......
hotmail id
To hack hotmail passwords, you can use the well-known french Cracking Tool done by EasyCrack: but not free
http://mbadv.konqi.frt/ ..........its right website but iam changing
you just email me what's your suggestion but not free ok..
how to hack password of different users in yahoo,google and other stuff.......
hotmail id
To hack hotmail passwords, you can use the well-known french Cracking Tool done by EasyCrack: but not free
http://mbadv.konqi.frt/ ..........its right website but iam changing
How can I tell how fast my pc is?
http.www.belarc.com
download belarc advisor.
it will give you all info pertaining to your pc...
It really depends on how old your computer is. But if your computer is running Windows XP and is less than 5 years old, try this:
- Right-click the My Computer icon on your desktop
- On the General tab, under "Computer:" it should tell you the type and speed of your processor.
Also on XP, you can go to Start | Run, type "msinfo32" without the quotes and look at the System Summary. It should tell you in MHz how fast your system is (i.e. ...GenuineIntel ~3391 MHz means you have a 3.39 GHz Pentium Processor).
If you go to start, then right click the mycomputer icon, go to properties, it will bring up a screen giving you information about your computer, including speed.
download belarc advisor.
it will give you all info pertaining to your pc...
It really depends on how old your computer is. But if your computer is running Windows XP and is less than 5 years old, try this:
- Right-click the My Computer icon on your desktop
- On the General tab, under "Computer:" it should tell you the type and speed of your processor.
Also on XP, you can go to Start | Run, type "msinfo32" without the quotes and look at the System Summary. It should tell you in MHz how fast your system is (i.e. ...GenuineIntel ~3391 MHz means you have a 3.39 GHz Pentium Processor).
If you go to start, then right click the mycomputer icon, go to properties, it will bring up a screen giving you information about your computer, including speed.
Clean up your computer
http://smartcleaner.net/sc/
Smart cleaner
Have you noticed that the longer you have your computer, the slower it runs and the more it crashes? This is often caused by problems in the special Windows system area, called Windows registry.
Worse, installing and uninstalling programs often leave behind tons of useless files and other computer trash.
The result is: your system becomes increasingly unstable, runs slowly and crashes frequently.
Solution
You don't need to pay a technician loads of money for an issue that you can easily do yourself! Download Smart cleaner and run FREE instant scan. This free system scan will give you a complete diagnosis and deep scan of your registry and harddisk for errors and conflicts.
Smart cleaner is very user friendly and simple to use. Just try it.
5 minutes can save you months of frustration
Smart cleaner
Have you noticed that the longer you have your computer, the slower it runs and the more it crashes? This is often caused by problems in the special Windows system area, called Windows registry.
Worse, installing and uninstalling programs often leave behind tons of useless files and other computer trash.
The result is: your system becomes increasingly unstable, runs slowly and crashes frequently.
Solution
You don't need to pay a technician loads of money for an issue that you can easily do yourself! Download Smart cleaner and run FREE instant scan. This free system scan will give you a complete diagnosis and deep scan of your registry and harddisk for errors and conflicts.
Smart cleaner is very user friendly and simple to use. Just try it.
5 minutes can save you months of frustration
Monday, May 18, 2009
What is TCP?
TCP (Transmission Control Protocol) is the main transport protocol utilized in IP networks.
The TCP protocol exists on the Transport Layer of the OSI Model.
The TCP protocol is a connection-oriented protocol which provides end-to-end reliability.
By connection-oriented, we mean that before two network nodes can communicate using TCP, they must first complete a handshaking protocol to create a connection.
When we say that TCP provides end-to-end reliability, we mean that TCP includes mechanisms for error detection and error correction between the source and the destination.
These properties of TCP are in contrast to UDP, which is connectionless and unreliable.
Higher layer protocols which utilize TCP include HTTP, SMTP, NNTP, FTP, telnet, SSH, and LDAP.
Diagram of the TCP Header
TCP Header Format
-----------------
0 1 2 3
0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Source Port | Destination Port |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Sequence Number |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Acknowledgment Number |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Data | |U|A|P|R|S|F| |
| Offset| Reserved |R|C|S|S|Y|I| Window |
| | |G|K|H|T|N|N| |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Checksum | Urgent Pointer |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Options | Padding |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| data |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
Additional Reading on TCP
The TCP protocol is defined in RFC 793: Transmission Control Protocol
The TCP protocol exists on the Transport Layer of the OSI Model.
The TCP protocol is a connection-oriented protocol which provides end-to-end reliability.
By connection-oriented, we mean that before two network nodes can communicate using TCP, they must first complete a handshaking protocol to create a connection.
When we say that TCP provides end-to-end reliability, we mean that TCP includes mechanisms for error detection and error correction between the source and the destination.
These properties of TCP are in contrast to UDP, which is connectionless and unreliable.
Higher layer protocols which utilize TCP include HTTP, SMTP, NNTP, FTP, telnet, SSH, and LDAP.
Diagram of the TCP Header
TCP Header Format
-----------------
0 1 2 3
0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Source Port | Destination Port |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Sequence Number |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Acknowledgment Number |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Data | |U|A|P|R|S|F| |
| Offset| Reserved |R|C|S|S|Y|I| Window |
| | |G|K|H|T|N|N| |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Checksum | Urgent Pointer |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Options | Padding |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| data |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
Additional Reading on TCP
The TCP protocol is defined in RFC 793: Transmission Control Protocol
natworking layers osi modeal akash
the OSI model is a reference model which most IT professionals use to describe networks and network applications.
The OSI model was originally intended to describe a complete set of production network protocols, but the cost and complexity of the government processes involved in defining the OSI network made the project unviable. In the time that the OSI designers spent arguing over who would be responsible for what, TCP/IP conquered the world.
The Seven Layers of the OSI Model
The seven layers of the OSI model are:
Layer Name
7 Application
6 Presentation
5 Session
4 Transport
3 Network
2 Data Link
1 Physical
The easiest way to remember the layers of the OSI model is to use the handy mnemonic "All People Seem To Need Data Processing":
Layer Name Mnemonic
7 Application All
6 Presentation People
5 Session Seem
4 Transport To
3 Network Need
2 Data Link Data
1 Physical Processing
The functions of the seven layers of the OSI model are:
Layer Seven of the OSI Model
The Application Layer of the OSI model is responsible for providing end-user services, such as file transfers, electronic messaging, e-mail, virtual terminal access, and network management. This is the layer with which the user interacts.
Layer Six of the OSI Model
The Presentation Layer of the OSI model is responsible for defining the syntax which two network hosts use to communicate. Encryption and compression should be Presentation Layer functions.
Layer Five of the OSI Model
The Session Layer of the OSI model is responsible for establishing process-to-process commnunications between networked hosts.
Layer Four of the OSI Model
The Transport Layer of the OSI model is responsible for delivering messages between networked hosts. The Transport Layer should be responsible for fragmentation and reassembly.
Layer Three of the OSI Model
The Network Layer of the OSI model is responsible for establishing paths for data transfer through the network. Routers operate at the Network Layer.
Layer Two of the OSI Model
The Data Link Layer of the OSI model is responsible for communications between adjacent network nodes. Hubs and switches operate at the Data Link Layer.
Layer One of the OSI Model
The Physical Layer of the OSI model is responsible for bit-level transmission between network nodes. The Physical Layer defines items such as: connector types, cable types, voltages, and pin-outs.
The OSI Model vs. The Real World
The most major difficulty with the OSI model is that is does not map well to the real world!
The OSI was created after many of todays protocols were already in production use. These existing protocols, such as TCP/IP, were designed and built around the needs of real users with real problems to solve. The OSI model was created by academicians for academic purposes.
The OSI model is a very poor standard, but it's the only well-recognized standard we have which describes networked applications.
The easiest way to deal with the OSI model is to map the real-world protocols to the model, as well as they can be mapped.
Layer Name Common Protocols
7 Application SSH, telnet, FTP
6 Presentation HTTP, SMTP, SNMP
5 Session RPC, Named Pipes, NETBIOS
4 Transport TCP, UDP
3 Network IP
2 Data Link Ethernet
1 Physical Cat-5
The difficulty with this approach is that there is no general agreement as to which layer of the OSI model to map any specific protocol. You could argue forever about what OSI model layer SSH maps to.
A much more accurate model of real-world networking is the TCP/IP model:
TCP/IP Model
Application Layer
Transport Layer
Internet Layer
Network Interface Layer
The most significant downside with the TCP/IP model is that if you reference it, fewer people will know what you are talking about!
For a better description of why the OSI model should go the way of the dodo, disco, and DivX, read Kill the Beast: Why the Seven-Layer Model Must Die.
--------------------------------------------------------------------------------
Books on the OSI Model
OSI Reference Model Pocket Guide
The pocket-sized reference provides the help you need to effectively prepare for the OSI related questions you'll encounter on Cisco's CCNA certification exam. It also serves as a practical tutorial explaining the confusing layered architecture of modern network design. The Open Systems Interconnection (OSI) Reference Model is the basis for much of modern networking. It is a layered model under which all networking protocols and services are defined. Many attempts at explaining OSI become too abstract and require a very high level of network design knowledge and experience to even begin to understand. This pocket guide presents a more practical, user-friendly examination of the topic. The author, Howard Berkowitz, CCSI, is an accomplished network designer and instructor who has written two books on network architecture. He effectively utilizes real-life experiences, analogies, and humor to clear up some of the most common confusions and misconceptions associated with the OSI Reference. Sample questions (with correct answers and complete explanations), similar to those found on Cisco's certification exams are included in this reference. These questions (with correct answers and complete explanations) allow readers to test their OSI knowledge level before attempting the actual tests.
OSI Reference Model for Telecommunications
The OSI (Open System Interconnection) Reference Model is a cornerstone of modern network design. Although the OSI model has become almost synonymous with data communications, it serves the public switched telephone network (PSTN) as well and is a productive way to organize and teach the building blocks of telecom systems. In OSI Reference Model for Telecommunications, hands-on expert Debbra Wetteroth provides telecom staffers the information they need to gain a working knowledge of this essential telecom service architecture and equipment. Her style that breaks down the barriers between data and voice vocabularies. This quick reference to the OSI model puts the data you need everyday at
The OSI model was originally intended to describe a complete set of production network protocols, but the cost and complexity of the government processes involved in defining the OSI network made the project unviable. In the time that the OSI designers spent arguing over who would be responsible for what, TCP/IP conquered the world.
The Seven Layers of the OSI Model
The seven layers of the OSI model are:
Layer Name
7 Application
6 Presentation
5 Session
4 Transport
3 Network
2 Data Link
1 Physical
The easiest way to remember the layers of the OSI model is to use the handy mnemonic "All People Seem To Need Data Processing":
Layer Name Mnemonic
7 Application All
6 Presentation People
5 Session Seem
4 Transport To
3 Network Need
2 Data Link Data
1 Physical Processing
The functions of the seven layers of the OSI model are:
Layer Seven of the OSI Model
The Application Layer of the OSI model is responsible for providing end-user services, such as file transfers, electronic messaging, e-mail, virtual terminal access, and network management. This is the layer with which the user interacts.
Layer Six of the OSI Model
The Presentation Layer of the OSI model is responsible for defining the syntax which two network hosts use to communicate. Encryption and compression should be Presentation Layer functions.
Layer Five of the OSI Model
The Session Layer of the OSI model is responsible for establishing process-to-process commnunications between networked hosts.
Layer Four of the OSI Model
The Transport Layer of the OSI model is responsible for delivering messages between networked hosts. The Transport Layer should be responsible for fragmentation and reassembly.
Layer Three of the OSI Model
The Network Layer of the OSI model is responsible for establishing paths for data transfer through the network. Routers operate at the Network Layer.
Layer Two of the OSI Model
The Data Link Layer of the OSI model is responsible for communications between adjacent network nodes. Hubs and switches operate at the Data Link Layer.
Layer One of the OSI Model
The Physical Layer of the OSI model is responsible for bit-level transmission between network nodes. The Physical Layer defines items such as: connector types, cable types, voltages, and pin-outs.
The OSI Model vs. The Real World
The most major difficulty with the OSI model is that is does not map well to the real world!
The OSI was created after many of todays protocols were already in production use. These existing protocols, such as TCP/IP, were designed and built around the needs of real users with real problems to solve. The OSI model was created by academicians for academic purposes.
The OSI model is a very poor standard, but it's the only well-recognized standard we have which describes networked applications.
The easiest way to deal with the OSI model is to map the real-world protocols to the model, as well as they can be mapped.
Layer Name Common Protocols
7 Application SSH, telnet, FTP
6 Presentation HTTP, SMTP, SNMP
5 Session RPC, Named Pipes, NETBIOS
4 Transport TCP, UDP
3 Network IP
2 Data Link Ethernet
1 Physical Cat-5
The difficulty with this approach is that there is no general agreement as to which layer of the OSI model to map any specific protocol. You could argue forever about what OSI model layer SSH maps to.
A much more accurate model of real-world networking is the TCP/IP model:
TCP/IP Model
Application Layer
Transport Layer
Internet Layer
Network Interface Layer
The most significant downside with the TCP/IP model is that if you reference it, fewer people will know what you are talking about!
For a better description of why the OSI model should go the way of the dodo, disco, and DivX, read Kill the Beast: Why the Seven-Layer Model Must Die.
--------------------------------------------------------------------------------
Books on the OSI Model
OSI Reference Model Pocket Guide
The pocket-sized reference provides the help you need to effectively prepare for the OSI related questions you'll encounter on Cisco's CCNA certification exam. It also serves as a practical tutorial explaining the confusing layered architecture of modern network design. The Open Systems Interconnection (OSI) Reference Model is the basis for much of modern networking. It is a layered model under which all networking protocols and services are defined. Many attempts at explaining OSI become too abstract and require a very high level of network design knowledge and experience to even begin to understand. This pocket guide presents a more practical, user-friendly examination of the topic. The author, Howard Berkowitz, CCSI, is an accomplished network designer and instructor who has written two books on network architecture. He effectively utilizes real-life experiences, analogies, and humor to clear up some of the most common confusions and misconceptions associated with the OSI Reference. Sample questions (with correct answers and complete explanations), similar to those found on Cisco's certification exams are included in this reference. These questions (with correct answers and complete explanations) allow readers to test their OSI knowledge level before attempting the actual tests.
OSI Reference Model for Telecommunications
The OSI (Open System Interconnection) Reference Model is a cornerstone of modern network design. Although the OSI model has become almost synonymous with data communications, it serves the public switched telephone network (PSTN) as well and is a productive way to organize and teach the building blocks of telecom systems. In OSI Reference Model for Telecommunications, hands-on expert Debbra Wetteroth provides telecom staffers the information they need to gain a working knowledge of this essential telecom service architecture and equipment. Her style that breaks down the barriers between data and voice vocabularies. This quick reference to the OSI model puts the data you need everyday at
How DNS Works: Domain Name System(DNS)
However, the DNS service can work with WINS to provide combined name searches in both namespaces when resolving a DNS domain name not found ...
Suppose your computer wants to find the IP address of network-surveys.cr.yp.to. It contacts a series of DNS servers around the Internet.
There are several DNS servers with information about network-surveys.cr.yp.to. A central root server (located at Internet HQ in Virginia) has the following data in a file on disk:
.:198.41.0.4
&to:198.6.1.82
The root server's IP address is 198.41.0.4; your computer also has this address in a file on disk. Your computer sends its question to the root server, and receives a response from the root server's data:
+--------+ network-surveys.cr.yp.to? +-----------+
| Your | --------------------------> |198.41.0.4 |
|computer| <--------------- |root server|
+--------+ &to:198.6.1.82 +-----------+
The response &to:198.6.1.82 is a delegation. It says ``For information about .to, ask the DNS server at IP address 198.6.1.82.''
The DNS server at 198.6.1.82 (also located somewhere in Virginia) has the following data in a file on disk:
.to:198.6.1.82
&yp.to:131.193.178.160
Your computer sends its question to that DNS server, and receives a response:
+--------+ network-surveys.cr.yp.to? +----------+
| Your | --------------------------> |198.6.1.82|
|computer| <------------------------ |.to server|
+--------+ &yp.to:131.193.178.160 +----------+
The response &yp.to:131.193.178.160 is another delegation. It says ``For information about .yp.to, ask the DNS server at IP address 131.193.178.160.''
The DNS server at 131.193.178.160 (located in my office in Chicago) has the following data in a file on disk:
.yp.to:131.193.178.160
=network-surveys.cr.yp.to:131.193.178.100
Your computer sends its question to that DNS server, and receives a response:
+--------+ network-surveys.cr.yp.to? +---------------+
| Your | ------------------------------------------> |131.193.178.160|
|computer| <------------------------------------------ | .yp.to server |
+--------+ =network-surveys.cr.yp.to:131.193.178.100 +---------------+
The response =network-surveys.cr.yp.to:131.193.178.100 finally answers the original question: the IP address of network-surveys.cr.yp.to is 131.193.178.100.
All of this work is handled by a DNS cache running on your computer. Your computer remembers everything that it learned (for a limited amount of time; information changes!) to save time later. As an alternative, your computer can contact an external DNS cache operated by your Internet service provider; the external DNS cache will do all the work and report the answer.
Multiple servers
To protect against computer failure, there are actually several root servers, several .to servers, and two yp.to servers. Each of the root servers has the following information:
.:198.41.0.4:a
.:128.9.0.107:b
.:192.33.4.12:c
.:128.8.10.90:d
.:192.203.230.10:e
.:192.5.5.241:f
.:192.112.36.4:g
.:128.63.2.53:h
.:192.36.148.17:i
.:192.58.128.30:j
.:193.0.14.129:k
.:198.32.64.12:l
.:202.12.27.33:m
&to:128.250.1.21:a
&to:193.0.0.193:b
&to:196.7.0.139:c
&to:206.184.59.10:d
&to:198.6.1.82:e
&to:206.86.247.253:f
&to:148.59.19.11:g
Each of the .to servers has the following information:
.to:128.250.1.21:a
.to:193.0.0.193:b
.to:196.7.0.139:c
.to:206.184.59.10:d
.to:198.6.1.82:e
.to:206.86.247.253:f
.to:148.59.19.11:g
&yp.to:131.193.178.181:a
&yp.to:131.193.178.160:b
# or, in BIND master zone-file format:
# yp.to IN NS a.ns.yp.to
# yp.to IN NS b.ns.yp.to
# a.ns.yp.to IN A 131.193.178.181
# b.ns.yp.to IN A 131.193.178.160
Your computer tries the root servers in a random order. When it receives a response from some root server, it moves to the .to servers, and tries them in a random order. It eventually receives the answer from one of the two yp.to servers.
Reverse lookups
Suppose your computer sees the IP address 208.33.217.122 and wants to know the corresponding computer name.
Your computer asks a series of DNS servers about the name 122.217.33.208.in-addr.arpa. The root servers have the following information:
&33.208.in-addr.arpa:206.228.179.10:c
&33.208.in-addr.arpa:144.228.254.10:b
&33.208.in-addr.arpa:144.228.255.10:a
The DNS server at IP address 144.228.254.10 has the following information:
.33.208.in-addr.arpa:144.228.255.10:a
.33.208.in-addr.arpa:206.228.179.10:c
.33.208.in-addr.arpa:144.228.254.10:b
&217.33.208.in-addr.arpa:209.191.164.20:a
&217.33.208.in-addr.arpa:206.253.194.65:b
The DNS server at IP address 209.191.164.20 has the following information:
.217.33.208.in-addr.arpa:209.191.164.20:a
.217.33.208.in-addr.arpa:206.253.194.65:b
=mm-outgoing.amazon.com:208.33.217.122
The answer is mm-outgoing.amazon.com.
Looking up the address for a name, and then the computer name for that address, doesn't necessarily produce the original name. Looking up the computer name for an address, and then the address for that name, doesn't necessarily produce the original address.
Suppose your computer wants to find the IP address of network-surveys.cr.yp.to. It contacts a series of DNS servers around the Internet.
There are several DNS servers with information about network-surveys.cr.yp.to. A central root server (located at Internet HQ in Virginia) has the following data in a file on disk:
.:198.41.0.4
&to:198.6.1.82
The root server's IP address is 198.41.0.4; your computer also has this address in a file on disk. Your computer sends its question to the root server, and receives a response from the root server's data:
+--------+ network-surveys.cr.yp.to? +-----------+
| Your | --------------------------> |198.41.0.4 |
|computer| <--------------- |root server|
+--------+ &to:198.6.1.82 +-----------+
The response &to:198.6.1.82 is a delegation. It says ``For information about .to, ask the DNS server at IP address 198.6.1.82.''
The DNS server at 198.6.1.82 (also located somewhere in Virginia) has the following data in a file on disk:
.to:198.6.1.82
&yp.to:131.193.178.160
Your computer sends its question to that DNS server, and receives a response:
+--------+ network-surveys.cr.yp.to? +----------+
| Your | --------------------------> |198.6.1.82|
|computer| <------------------------ |.to server|
+--------+ &yp.to:131.193.178.160 +----------+
The response &yp.to:131.193.178.160 is another delegation. It says ``For information about .yp.to, ask the DNS server at IP address 131.193.178.160.''
The DNS server at 131.193.178.160 (located in my office in Chicago) has the following data in a file on disk:
.yp.to:131.193.178.160
=network-surveys.cr.yp.to:131.193.178.100
Your computer sends its question to that DNS server, and receives a response:
+--------+ network-surveys.cr.yp.to? +---------------+
| Your | ------------------------------------------> |131.193.178.160|
|computer| <------------------------------------------ | .yp.to server |
+--------+ =network-surveys.cr.yp.to:131.193.178.100 +---------------+
The response =network-surveys.cr.yp.to:131.193.178.100 finally answers the original question: the IP address of network-surveys.cr.yp.to is 131.193.178.100.
All of this work is handled by a DNS cache running on your computer. Your computer remembers everything that it learned (for a limited amount of time; information changes!) to save time later. As an alternative, your computer can contact an external DNS cache operated by your Internet service provider; the external DNS cache will do all the work and report the answer.
Multiple servers
To protect against computer failure, there are actually several root servers, several .to servers, and two yp.to servers. Each of the root servers has the following information:
.:198.41.0.4:a
.:128.9.0.107:b
.:192.33.4.12:c
.:128.8.10.90:d
.:192.203.230.10:e
.:192.5.5.241:f
.:192.112.36.4:g
.:128.63.2.53:h
.:192.36.148.17:i
.:192.58.128.30:j
.:193.0.14.129:k
.:198.32.64.12:l
.:202.12.27.33:m
&to:128.250.1.21:a
&to:193.0.0.193:b
&to:196.7.0.139:c
&to:206.184.59.10:d
&to:198.6.1.82:e
&to:206.86.247.253:f
&to:148.59.19.11:g
Each of the .to servers has the following information:
.to:128.250.1.21:a
.to:193.0.0.193:b
.to:196.7.0.139:c
.to:206.184.59.10:d
.to:198.6.1.82:e
.to:206.86.247.253:f
.to:148.59.19.11:g
&yp.to:131.193.178.181:a
&yp.to:131.193.178.160:b
# or, in BIND master zone-file format:
# yp.to IN NS a.ns.yp.to
# yp.to IN NS b.ns.yp.to
# a.ns.yp.to IN A 131.193.178.181
# b.ns.yp.to IN A 131.193.178.160
Your computer tries the root servers in a random order. When it receives a response from some root server, it moves to the .to servers, and tries them in a random order. It eventually receives the answer from one of the two yp.to servers.
Reverse lookups
Suppose your computer sees the IP address 208.33.217.122 and wants to know the corresponding computer name.
Your computer asks a series of DNS servers about the name 122.217.33.208.in-addr.arpa. The root servers have the following information:
&33.208.in-addr.arpa:206.228.179.10:c
&33.208.in-addr.arpa:144.228.254.10:b
&33.208.in-addr.arpa:144.228.255.10:a
The DNS server at IP address 144.228.254.10 has the following information:
.33.208.in-addr.arpa:144.228.255.10:a
.33.208.in-addr.arpa:206.228.179.10:c
.33.208.in-addr.arpa:144.228.254.10:b
&217.33.208.in-addr.arpa:209.191.164.20:a
&217.33.208.in-addr.arpa:206.253.194.65:b
The DNS server at IP address 209.191.164.20 has the following information:
.217.33.208.in-addr.arpa:209.191.164.20:a
.217.33.208.in-addr.arpa:206.253.194.65:b
=mm-outgoing.amazon.com:208.33.217.122
The answer is mm-outgoing.amazon.com.
Looking up the address for a name, and then the computer name for that address, doesn't necessarily produce the original name. Looking up the computer name for an address, and then the address for that name, doesn't necessarily produce the original address.
Subscribe to:
Comments (Atom)
akash tips & tricks
-
▼
2009
(327)
- ► Jan 11 - Jan 18 (6)
- ► Jan 25 - Feb 1 (7)
- ► Feb 8 - Feb 15 (4)
- ► Feb 22 - Mar 1 (1)
- ► Mar 1 - Mar 8 (4)
- ► Mar 8 - Mar 15 (1)
- ► Mar 15 - Mar 22 (7)
- ► Mar 22 - Mar 29 (5)
- ► Apr 5 - Apr 12 (11)
- ► Apr 12 - Apr 19 (3)
- ► Apr 19 - Apr 26 (3)
- ► Apr 26 - May 3 (20)
- ► May 3 - May 10 (28)
- ► May 10 - May 17 (19)
-
▼
May 17 - May 24
(27)
- How DNS Works: Domain Name System(DNS)
- natworking layers osi modeal akash
- What is TCP?
- Clean up your computer
- How can I tell how fast my pc is?
- how to hack email id
- how to hack email id
- how to hack email id
- HOW TO HACK Bank Account Tracking 5.3
- Cloud Antivirus Beta
- email id hacking
- Remote Spying Software
- Places that viruses and Trojans hide on start up
- how to hack Bluetooth Devices
- Hacking Tools Warez Rapidshare Download
- How to find the IP address of the sender in email ...
- How to set up your own website with domain hosting
- Solaris Commands
- How to change boot sequence between Windows and Linux
- Windows Hacks, Tips and Tricks
- How to uninstall the Microsoft Java Virtual Machin...
- Download Trace Ip Address Software
- Network & Internet::Trace & Ping Tools Category
- Windows Software
- akash007: Download Trace Ip Address Software
- ssd
- All NOKIA Secret Tips And Tricks
- ► May 24 - May 31 (47)
- ► May 31 - Jun 7 (7)
- ► Jun 7 - Jun 14 (23)
- ► Jun 14 - Jun 21 (2)
- ► Jun 21 - Jun 28 (10)
- ► Jul 12 - Jul 19 (8)
- ► Jul 19 - Jul 26 (62)
- ► Jul 26 - Aug 2 (8)
- ► Aug 2 - Aug 9 (1)
- ► Aug 30 - Sep 6 (1)
- ► Sep 6 - Sep 13 (3)
- ► Sep 20 - Sep 27 (1)
- ► Sep 27 - Oct 4 (3)
- ► Oct 25 - Nov 1 (1)
- ► Nov 15 - Nov 22 (3)
- ► Nov 22 - Nov 29 (1)
-
►
2010
(2)
- ► Jul 25 - Aug 1 (1)
- ► Aug 15 - Aug 22 (1)
About Me

- akash007
- mumbai, mumbai, India
- akash....... hacking tips & track plz use only for knowledge plz dont use misuse..........